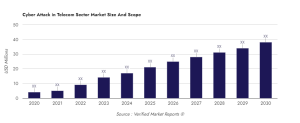
The Global Cyber Attack in Telecom Sector Market is projected to grow at a rate of 10.5% and reach USD 4,068.5 million by 2027. This growth is fueled by an increase in cyber-attacks, the adoption of cloud computing and data analytics technologies, and the growing number of connected devices. However, challenges include a shortage of skilled professionals and the high cost of cyber security solutions. On the bright side, government initiatives such as regulations and guidelines from the European Union present new opportunities for the market.
A cyber attack in telecom occurs when someone deliberately steals, disrupts, or exploits data or networks in the telecom industry. This can involve activities such as phishing, malware, ransomware, malicious domain registration, DDoS attacks, and other harmful actions that aim to compromise the security of telecom companies and their customers.
The Global Cyber Attack in Telecom Sector Market is mainly caused by the increase in cyber-attacks and the use of technologies like cloud computing, data analytics, and connected devices. This is leading to market growth as organizations invest in cyber security solutions to protect their data and networks. The market is also expected to benefit from the opportunities arising from the emergence of 5G technology.
The Global Cyber Attack in the Telecom Sector Market has two main challenges. The first is a lack of skilled personnel to implement the necessary cyber security solutions. The second challenge is the high cost of these solutions, which limits market growth because organizations cannot afford them.
Government actions are supporting the growth of the Global Telecom Sector Market in Cyber Attack. For instance, the European Union has put in place regulations and guidelines to protect its citizens from cyber-attacks. Additionally, governments are providing financial help to organizations to improve their cyber security infrastructure.
This report examines the global cyber attack in the telecom sector market. It includes information about the market size, trends, growth drivers, restraints, competition, regional analysis, and other relevant factors. Market experts and reputable sources such as the World Bank, ITU, and OECD have provided valuable insights.
Growth driving factors of the Global Cyber Attack in Telecom Sector Market
- The increasing complexity of networks and systems globally is a major cause of cyber attacks in the telecom sector. As technology advances, networks and systems become more complex, which makes them more susceptible to cyber threats. Attackers take advantage of this complexity to bypass security measures and access sensitive data without permission. Moreover, monitoring complex networks is challenging, making them an easier target for attackers.
- The increasing number of connected devices and endpoints is driving cyber attacks in the telecom sector. As more and more devices connect to the internet, the risk of cyber security threats also increases. Attackers can target a largeacyber security threats.
- Lack of adequate security measures
- Growing adoption of cloud computing and virtualization
- Increased usage of mobile devices and demand for data access
Global Cyber Attack in Telecom Sector Market Segment Insights
The Global Cyber Attack in the Telecom Sector Market is segmented based on Product/Type, Application, Deployment, Organization.
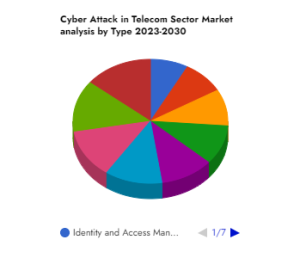
By Product/Type
Identity and Access Management
Risk and Compliance Management
Encryption
Data Loss Prevention
Unified Threat Management
Firewall
Antivirus/Anti-Malware
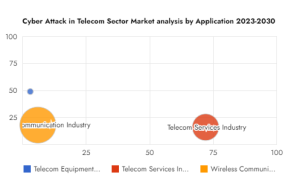
By Application
Telecom Equipment Industry
Telecom Services Industry
Wireless Communication Industry
By Deployment
On-Premise
Cloud-Based
By Organization Size
Small and Medium Enterprises
Large Enterprises
Global Cyber Attack in Telecom Sector Market Regional Analysis
North America
Europe
Asia
Middle East
Latin America
Asia
Cyber attacks pose a growing threat to the telecom sector in Asia due to the rise of digital technologies and the increasing skill of cyber criminals. Telecom networks in the region have been targeted by a significant number of attacks, many of which come from China, India, and other Asian countries.
The attacks have caused telecom companies in the region to lose money, suffer damage to their reputation, and experience service disruptions. Customer data has also been stolen, making the situation even worse. The cyber attack market in Asia is growing due to several factors, including more advanced cyber criminals, the availability of sophisticated tools, and inadequate security measures.
The region has a big population and many telecom companies, making it a target for cyber criminals. To fight cyber attacks, telecom companies need to invest in strong security measures for their networks. They also need to protect their customers’ data and ensure that their services are not affected. This will keep the telecommunications sector in Asia safe and strong.
Source: verifiedmarketreports
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind