There has been a 53 per cent increase in ransomware incidents in India in 2022 when compared to 2021, the Indian Computer Emergency Response Team (CERT-In) said in a report.
The CERT-In, in its India Ransomware Report released on April 13, said, in 2022, among various sectors, IT and ITeS was majorly impacted followed by finance and manufacturing.
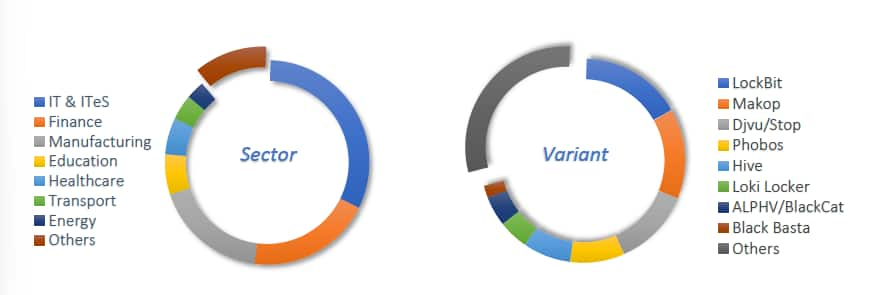 Source: CERT-In
Source: CERT-In
CERT-In observed that the motivation towards perpetrating ransomware attacks was not just money, but also “geo political conflicts”. “This trend may continue further when ransomware broadens its spectrum beyond financial aspects and becomes an arsenal for cyberwarfares,” the report said.
The nodal cybersecurity agency of the country also observed that phishing was a major point of initial network access for attackers, apart from them exploiting known vulnerabilities in applications and systems.
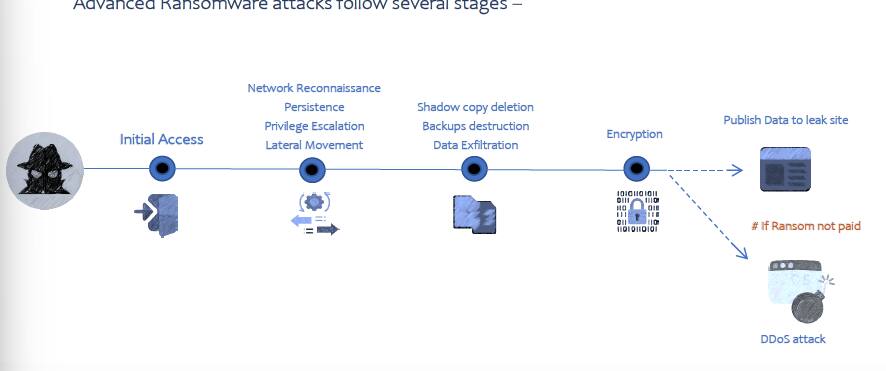 How ransomwares work (Source: CERT-In)
How ransomwares work (Source: CERT-In)
“In addition, system misconfigurations, brute force attacks, unmanaged devices, insider threats and supply chain attacks are becoming concerning risk factors,” the report added.
This report comes at a time when Indian government websites have been reported of being targeted by Indonesian hacktivists, and few months after All India Medical Institute of Medical Sciences suffered a major ransomware breach that rendered several of its services inaccessible.
Earlier the government had also informed in the Parliament that 19 ransomware attacks were recorded against various government organisations in 2022, which was almost three times of those in the previous year.
10 days to restore services
On an average, the CERT-In report found that, a large organisation, after suffering a ransomware attack, took about 10 days to restore.
“For smaller network/infrastructure, the restoration time is around 3 days and for individual systems it is 1 day,” it said.
The report further observed that ransomware gangs were deploying innovative tactics “to improve operational efficiency”.
“Some groups are rebranding themselves and some are carrying out low-profile attacks to avoid the attention of law enforcement,” the report said.
CERT-In urged organisations to shore up their capabilities for monitoring and early detection of ransomware infection.
“As prevention is better than cure, it is desirable to understand the attack surface and ensure hardening of all internet-exposed assets and improve security posture to minimise the Ransomware attack probability,” the report said.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind