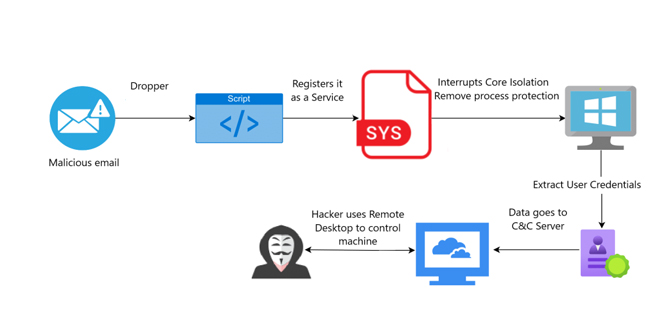
Threat actors are exploiting a component of CheckPoint’s ZoneAlarm antivirus to bypass Windows security measures. Nima Bagheri, a security researcher in Austin and founder of Venak Security, announced a new Bring Your Own Vulnerable Driver (BYOVD) attack in a report on March 20.
Threat actors exploited vulnerabilities in vsdatant.sys, a system file from ZoneAlarm software by CheckPoint Software Technologies.
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
By infosecbulletin
/ Sunday , June 15 2025
WestJet, Canada's second-largest airline, is looking into a cyberattack that has affected some internal systems during its response to the...
Read More
By infosecbulletin
/ Saturday , June 14 2025
Resecurity found 7.4 million records of Paraguayan citizens' personal information leaked on the dark web today. Last week, cybercriminals attempted...
Read More
By infosecbulletin
/ Friday , June 13 2025
HashiCorp has revealed a critical vulnerability in its Nomad tool that may let attackers gain higher privileges by misusing the...
Read More
By infosecbulletin
/ Friday , June 13 2025
SoftBank has disclosed that personal information of more than 137,000 mobile subscribers—covering names, addresses, and phone numbers—might have been leaked...
Read More
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
Conditions for BYOVD Attack:
Like many endpoint security solutions, vsdatant.sys has high-level access, allowing it to reach and change important system parts, intercept system actions, and possibly avoid security measures, giving it a high level of control over an operating system.
The driver is legitimate and has a valid signature, so antivirus and EDR solutions usually consider its activity safe.
These two conditions are the building blocks of a successful BYOVD attack.
Bypassing Windows Memory Integrity Security Protection:
Bagheri’s report indicated that vsdatant.sys version 14.1.32.0, released in 2016, has multiple vulnerabilities, though he did not specify what they are.
Threat actors exploited vulnerabilities to bypass Windows Memory Integrity, a feature that protects critical system processes by isolating them in a virtual environment, making it difficult for attackers to inject malicious code.
“Once these defenses were bypassed, attackers had full access to the underlying system, the attackers were able to access sensitive information such as user passwords and other stored credentials. This data was then exfiltrated, opening the door for further exploitation,” Bagheri continued.
The attackers set up a Remote Desktop Protocol (RDP) connection to the infected systems, allowing them ongoing access to the compromised machines.
Bagheri stated that the latest version of vsdatant.sys is secure, advising CheckPoint ZoneAlarm customers to update to it if they can.
The security researcher contacted CheckPoint before publishing the report.
Source: venaksecurity
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind