A vulnerability in the Cisco ACI Multi-Site CloudSec encryption feature of Cisco Nexus 9000 Series Fabric Switches in ACI mode could allow an unauthenticated, remote attacker to read or modify intersite encrypted traffic.
This vulnerability is due to an issue with the implementation of the ciphers that are used by the CloudSec encryption feature on affected switches. An attacker with an on-path position between the ACI sites could exploit this vulnerability by intercepting intersite encrypted traffic and using cryptanalytic techniques to break the encryption. A successful exploit could allow the attacker to read or modify the traffic that is transmitted between the sites.
Cisco has not released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
ALSO READ:
Microsoft Teams exploiting tool on GitHub, What Microsoft say?
Affected Products
Vulnerable Products
This vulnerability affects Cisco Nexus 9000 Series Fabric Switches in ACI mode that are running releases 14.0 and later if they are part of a Multi-Site topology and have the CloudSec encryption feature enabled.
Determine the Status of the CloudSec Feature
CloudSec encryption currently requires using Cisco Nexus 9332C or Cisco Nexus 9364C Fixed Spine Switches, or Cisco Nexus 9500 Spine Switches that are equipped with a Cisco Nexus N9K-X9736C-FX Line Card.
To determine whether CloudSec encryption is in use in an ACI site, choose Infrastructure > Site Connectivity > Configure > Sites > site-name > Inter-Site Connectivity on the Cisco Nexus Dashboard Orchestrator (NDO) and check if CloudSec Encryption is marked Enabled.
To determine whether CloudSec encryption is in use on a Cisco Nexus 9000 Series Spine Switch, use the show cloudsec sa interface all command at the switch CLI. If the command returns Operational Status output for any interface, CloudSec encryption is enabled, as shown in the following example:
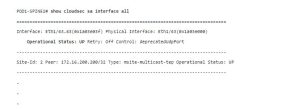
Cisco has confirmed that this vulnerability does not affect Cisco Nexus 9000 Series Switches in standalone NX-OS mode.
Fixed Software
Cisco has not released software updates to address the vulnerability that is described in the advisory. Customers who are currently using the Cisco ACI Multi-Site CloudSec encryption feature for the Cisco Nexus 9332C and Nexus 9364C Switches and the Cisco Nexus N9K-X9736C-FX Line Card are advised to disable it and to contact their support organization to evaluate alternative options.
When considering software upgrades, customers are advised to regularly consult the advisories for Cisco products, which are available from the Cisco Security Advisories page, to determine exposure and a complete upgrade solution.
In all cases, customers should ensure that the devices to be upgraded contain sufficient memory and confirm that current hardware and software configurations will continue to be supported properly by the new release. If the information is not clear, customers are advised to contact the Cisco Technical Assistance Center (TAC) or their contracted maintenance providers.
For detail click here
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














