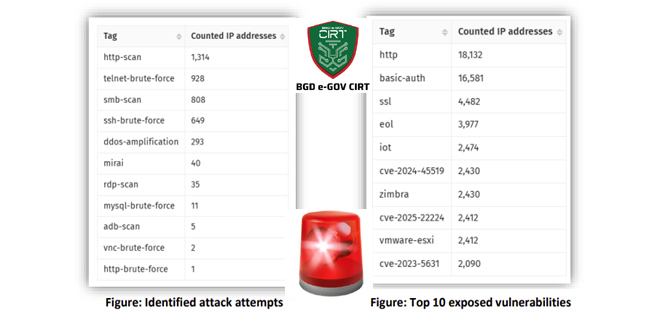
As the Eid holidays near, cybercriminals may try to take advantage of weakened security during this time. The CTI unit of BGD e-GOV CIRT has identified several web-based attacks, especially during non-office hours and holidays. Common attack methods include SSH brute force, SQL injection, PHP CGI-bin exploits, and directory traversal attacks, all seeking unauthorized access.
In the past week, several cyberattacks targeting Bangladesh have been reported. Notably, 26,887 IP addresses were found to have exposed vulnerabilities, raising the risk of exploitation.
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
By infosecbulletin
/ Sunday , June 15 2025
WestJet, Canada's second-largest airline, is looking into a cyberattack that has affected some internal systems during its response to the...
Read More
By infosecbulletin
/ Saturday , June 14 2025
Resecurity found 7.4 million records of Paraguayan citizens' personal information leaked on the dark web today. Last week, cybercriminals attempted...
Read More
By infosecbulletin
/ Friday , June 13 2025
HashiCorp has revealed a critical vulnerability in its Nomad tool that may let attackers gain higher privileges by misusing the...
Read More
By infosecbulletin
/ Friday , June 13 2025
SoftBank has disclosed that personal information of more than 137,000 mobile subscribers—covering names, addresses, and phone numbers—might have been leaked...
Read More
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
CIRT advises all organizations in Bangladesh to implement the following measures to strengthen the security of their infrastructure:
Maintain 24/7 monitoring of systems and networks.
Keep security tools like SIEM, IDS/IPS, and WAF active for threat detection.
Use only approved VPNs and MFA for remote access.
Restrict connections from public or unsecured networks.
Prohibit outdated or unpatched software.
Ensure secure backups for critical data and prepare for disaster recovery.
Limit access, especially during holidays, and disable unused or temporary accounts.
Report incidents to relevant cybersecurity authorities, including detection of IOCs.
Micropatches released for Windows zero-day leaking NTLM hashes
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind