Lumen Technologies’ malware hunters have discovered Chinese APT group Volt Typhoon using a new zero-day exploit in Versa Director servers. They used this exploit to steal credentials and gain unauthorized access to the networks of downstream customers.
CVE-2024-39717 is a serious vulnerability that CISA added to their must-patch list after Versa Networks confirmed zero-day exploitation. They warned that the Versa Director GUI can be hacked to plant malware on affected devices.
Versa Director servers are important for managing network configurations for clients using SD-WAN software. They are heavily used by ISPs and MSPs, which makes them a prime target for threat actors looking to expand their influence within enterprise network management.
“Versa Networks is aware of one confirmed customer reported instance where this vulnerability was exploited because the Firewall guidelines which were published in 2015 and 2017 were not implemented by that customer. This non-implementation resulted in the bad actor being able to exploit this vulnerability without using the GUI,” the company said, appearing to pass blame on victim organizations for misconfiguration errors.
“In our testing (not exhaustive, as not all numerical versions of major browsers were tested) the malicious file does not get executed on the client. There are reports of others based on backbone telemetry observations of a 3rd party provider, however these are unconfirmed to date,” Versa said in a security bulletin.
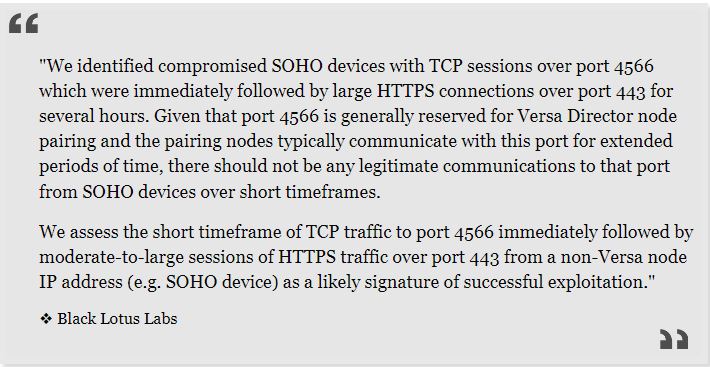
Lumen Technologies’ Black Lotus Labs team found that there is active exploitation of a vulnerability in older versions of Versa Director, specifically versions prior to 22.1.4.
The team found a special web shell that is used to steal login information and gain access to other networks.
The Black Lotus Labs team has connected the zero-day exploit to Volt Typhoon, a hacking group supported by the Chinese government. Volt Typhoon has carried out numerous attacks on critical infrastructure targets in the United States. The company believes that only Volt Typhoon is using this vulnerability to attack unpatched Versa Director systems.
The researchers identified vulnerabilities dating back to at least June 12, 2024. They warn that this Volt Typhoon campaign targets specific victims in the ISP, MSP, and IT sectors in the US.
Volt Typhoon, which started in mid-2021, has targeted many different organizations in sectors such as communications, manufacturing, utilities, transportation, construction, maritime, government, information technology, and education.
Black Lotus Lab researchers have discovered Volt Typhoon hackers in network devices previously. Last December, they raised an alarm about a large botnet using end-of-life Cisco, Netgear, and Fortinet devices as covert data transfer networks for malicious operations.
One month later, the US government stopped the botnet and encouraged organizations to work harder to remove Chinese hackers from hijacked networks.
The Black Lotus Labs team will release detailed technical documentation this week, including Indicators of Compromise (IOCs) and telemetry data to assist organizations in detecting signs of compromise.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














