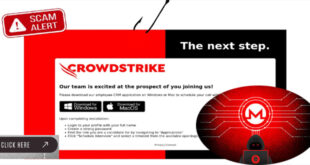
In a sophisticated phishing campaign, uncovered cybercriminals are exploiting CrowdStrike’s recruitment branding to target developers and deploy the XMRig cryptominer. This scam uses fake job offers to trick victims into downloading harmful software disguised as an “employee CRM application.” The attack starts with a phishing email pretending to be from …
Read More »Palo Alto Networks Expedition Tool Vuln Lead to Exposure of Firewall Credentials
Palo Alto Networks released a security advisory about vulnerabilities in its Expedition migration tool that could expose sensitive data and enable unauthorized actions on affected systems. Expedition, formerly the Migration Tool, is a free tool that helps users migrate to the Palo Alto Networks NGFW platform and provides a temporary …
Read More »Best Cybersecurity Certifications for Your Career in 2025
Cybersecurity professionals serve as the first line of defense against hackers, hacktivists, and ransomware groups. To combat these cyber threats, there is an ever-growing need for skilled individuals who can effectively identify and mitigate cyber risks. As we enter 2025, both aspiring cybersecurity experts and seasoned professionals must stay informed …
Read More »City Bank Customer financial reports posted dark market for sale
According to Bangladesh Cyber Security Intelligence (BCSI) report, City Bank has been the victim of a cyber attack. The hacker group was selling the bank’s customer financial reports on a dark web market. BCSI has contacted the hacker. In the published report, BCSI shared screenshots of the conversation with the …
Read More »HIPAA to be updated with new cybersecurity regulations, White House
Proposed new cybersecurity rules for healthcare institutions will focus on how they protect user data under HIPAA, as stated by a White House official. Anne Neuberger, deputy national security adviser for cyber and emerging technology, told “The security rule [under HIPAA] was first published in 2003 and it was last …
Read More »
Update Immediately
Palo Alto Releases Patch for PAN-OS DoS Flaw
Palo Alto Networks has revealed a high severity vulnerability in PAN-OS software that may lead to a denial-of-service (DoS) issue on affected devices. The vulnerability CVE-2024-3393 (CVSS score: 8.7) affects PAN-OS versions 10.X and 11.X, and Prisma Access with PAN-OS versions 10.2.8 or later and before 11.2.3. It has been …
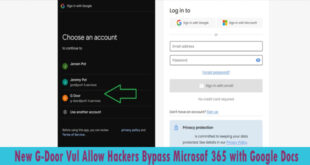
Read More »New G-Door Vul Allow Hackers Bypass Microsoft 365 Security With Google Docs
A newly discovered vulnerability called “G-Door” enables malicious actors to bypass Microsoft 365 security by exploiting unmanaged Google Docs accounts. This flaw poses a serious threat to organizations using Microsoft 365’s Conditional Access policies. The G-Door vulnerability stems from the ability to create personal or workspace Google accounts using a …
Read More »CISA released best practices to secure Microsoft 365 Cloud environments
CISA has issued Binding Operational Directive (BOD) 25-01, requiring federal civilian agencies to improve the security of their Microsoft 365 cloud environments. This directive is part of CISA’s effort to reduce risks from cloud misconfigurations and weak security controls that have been targeted in recent cyberattacks. BOD 25-01 introduces Secure …
Read More »Data breach! Ireland fines Meta $264 million, Australia $50m
The Irish Data Protection Commission fined Meta €251 million ($263.6 million) for GDPR violations related to a 2018 data breach that affected 29 million Facebook accounts. The breach occurred when unauthorized parties exploited user access tokens, exposing sensitive information like names, email addresses, phone numbers, and physical locations, including data …
Read More »GitLab flaw allow Bitcoin ATM giant “Byte Federal” hacked
TechCrunch reports that Byte Federal, a major Bitcoin ATM operator in the U.S., has experienced a data breach affecting the personal information of thousands of customers. A Florida-based company recently reported to the Maine attorney general that hackers tried to access data from about 58,000 customers. The breached information includes …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind