Amnesty International’s Security Lab discovered a cyber-espionage campaign in Serbia, where officials used a zero-day exploit from Cellebrite to unlock a student activist’s Android phone. On December 25, 2024, an attack used flaws in Linux kernel USB drivers to bypass the lock screen on a Samsung Galaxy A32. Forensic analysis …
Read More »DragonForce Ransomware Targets Saudi Company, 6TB Data Stolen
DragonForce ransomware targets organizations in Saudi Arabia. An attack on a major Riyadh real estate and construction firm led to the theft of more than 6TB of sensitive data. Resecurity’s new advisory reports that threat actors announced a breach on February 14, 2025, demanding ransom before releasing stolen information. The …
Read More »Microsoft Uncovers Hackers Selling Illegal Azure AI Access
Microsoft has filed an amended complaint in recent civil litigation, naming the main developers of malicious tools that bypass the safeguards of generative AI services, including its Azure OpenAI Service. The legal action aims to stop their actions, dismantle their illegal operation, and deter others from misusing AI technology. The …
Read More »By 2025, India’s First Semiconductor Chip to be ready
At the Global Investors Summit 2025, Union Minister Ashwini Vaishnaw announced that India’s first indigenous semiconductor chip will be ready for production by 2025, showcasing the significant growth of Madhya Pradesh’s electronics manufacturing sector. Minister Vaishnaw congratulated the HLBS family on their new plant’s inauguration, which coincided with Mahashivratri. He …
Read More »
CVE-2024-12284
Citrix Issues Security Update for NetScaler Console
Citrix has issued security updates for a serious vulnerability in the NetScaler Console and NetScaler Agent that could allow privilege escalation in specific situations. The vulnerability, identified as CVE-2024-12284, has been given a CVSS v4 score of 8.8 out of a maximum of 10.0 It involves improper handling of user …
Read More »
150 Gov.t Portal affected
Black-Hat SEO Poisoning Indian “.gov.in, .ac.in” domain
Indian government and educational websites, along with reputable financial brands, have experienced SEO poisoning, causing user traffic to be redirected to dubious sites promoting rummy and other investment games. Analysts at CloudSEK have found that threat actors are using black hat Search Engine Poisoning to promote Rummy and investment websites …
Read More »SonicWall Firewall Auth Bypass Vulnerability Exploited in Wild
A serious authentication bypass vulnerability in SonicWall firewalls, called CVE-2024-53704, is currently being exploited, according to cybersecurity firms. The increase in attacks is due to the public release of exploit code by Bishop Fox on February 10, 2025, which raises risks for organizations with unpatched devices. CVE-2024-53704, with a CVSS …
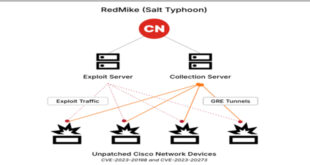
Read More »Salt Typhoon to target Bangladeshi Universities, One identified
RedMike (Salt Typhoon) targeted university devices in Bangladesh, likely to access research in telecommunications, engineering, and technology, especially from institutions like UCLA and TU Delft. Recorded Futureʼs Insikt Group identified the campaign targeted universities in various countries like Argentina, Indonesia, Malaysia, Mexico, the Netherlands, Thailand, the United States, and Vietnam. …
Read More »Salt Typhoon Exploits Vulnerable Cisco Devices of Telcoms Globally
Between December 2024 and January 2025, Recorded Future’s Insikt Group discovered a campaign targeting unpatched Cisco devices used by major telecommunications providers. Victims included a US affiliate of a major UK telecom and a South African telecom. Insikt Group links this activity to the Chinese state-sponsored group RedMike, also known …
Read More »
(CVE-2025-1146
CrowdStrike Fixed High-Severity TLS Vuln in Falcon Sensor
CrowdStrike has issued a security advisory for a serious TLS vulnerability, CVE-2025-1146, in its Falcon Sensor for Linux, Falcon Kubernetes Admission Controller, and Falcon Container Sensor. This vulnerability could enable man-in-the-middle (MiTM) attacks. CrowdStrike secures communications from the Falcon sensor to its cloud using standard TLS. However, a validation error …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind