A critical permission misconfiguration in the IBM QRadar Security Information and Event Management (SIEM) platform could allow local privileged users to manipulate configuration files without authorization. The flaw, identified as CVE-2025-0164, results from incorrect permission assignments and has a CVSS 3.1 score of 2.3 AV:L/AC:L/PR:H/UI:N/S:U/C:L/I:N/A:N). Incorrect Permission Assignment Flaw: The …
Read More »AI Pentesting Tool ‘Villager’ Merges Kali Linux with DeepSeek AI for Automated Attacks
The Villager framework, an AI-powered penetration testing tool, integrates Kali Linux tools with DeepSeek AI to automate cyber attack processes. Developed by the Chinese group Cyberspike, it was released on the Python Package Index in July 2025 and quickly gained over 10,000 downloads in two months. Villager marks a major …
Read More »
CVE-2025-21043
Samsung Patched Critical Zero-Day Flaw Exploited in Android Attacks
Samsung released its monthly Android security updates, addressing a vulnerability exploited in zero-day attacks. CVE-2025-21043 (CVSS score: 8.8) is a vulnerability that allows an out-of-bounds write, potentially leading to arbitrary code execution. “Out-of-bounds Write in libimagecodec.quram.so prior to SMR Sep-2025 Release 1 allows remote attackers to execute arbitrary code,” Samsung …
Read More »Palo Alto Networks User-ID Credential Agent Vuln Exposes password In Cleartext
A new vulnerability, CVE-2025-4235, in Palo Alto Networks’ User-ID Credential Agent for Windows, could reveal a service account’s password in cleartext with specific configurations. The vulnerability has been rated as having medium severity. The primary danger lies in the potential for privilege escalation. The impact of the vulnerability varies depending …
Read More »CyberVolk Ransomware Attacks CII In Japan, France, and UK
CyberVolk ransomware, which appeared in May 2024, has increased attacks on government agencies and critical infrastructures in Japan, France, and the UK. CyberVolk, with pro-Russian views, targets countries seen as threats to Russia using advanced encryption that is very hard to break. This article analyzes CyberVolk’s encryption system, its execution …
Read More »Microsoft warns of active directory and office vulnarability
Microsoft has issued a new warning about a critical security vulnerability in Active Directory Domain Services, known as CVE-2025-21293. An attacker with initial access could exploit this flaw to increase their privileges, gaining full control over the domain controller and compromising the network’s security. The vulnerability is categorized as an …
Read More »
(CVE-2025-10159)
Sophos Addressed Critical Auth Bypass flaw in Wireless Access Points
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The company found the issue during internal security tests and has issued a firmware update to fix it. An attacker with network access to the access point’s management IP can bypass …
Read More »Microsoft September Patch Tuesday 2025 fixes 81 flaws, two zero-days
Microsoft patched September 2025 Patch Tuesday 81 flaws, including two publicly disclosed zero-day vulnerabilities. This Patch Tuesday addresses nine critical vulnerabilities: five for remote code execution, one for information disclosure, and two for privilege escalation. The number of bugs in each vulnerability category is listed below: 41 Elevation of Privilege …
Read More »
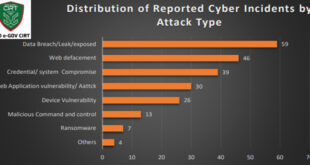
Bangladesh Cyber Threat Landscape- 2024
602 Vuln exploited: Afftected daily 905 IP In Bangladesh in 2024
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year saw a surge in ransomware, phishing, hacktivism, and data breaches, affecting both public and private sectors. Critical vulnerabilities in outdated systems, increased use of the dark web for trading stolen …
Read More »Mis-Issued TLS Certificate Exposes 1.1.1.1 DNS Services to Exploitation
Security researchers found that three unauthorized TLS certificates were issued in May 2025 for 1.1.1.1, the public DNS service operated by Cloudflare. Improperly issued certificates by the Fina RDC 2020 authority could let attackers intercept and decrypt DNS queries, revealing users’ browsing habits. However, if a malicious or unauthorized party …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind