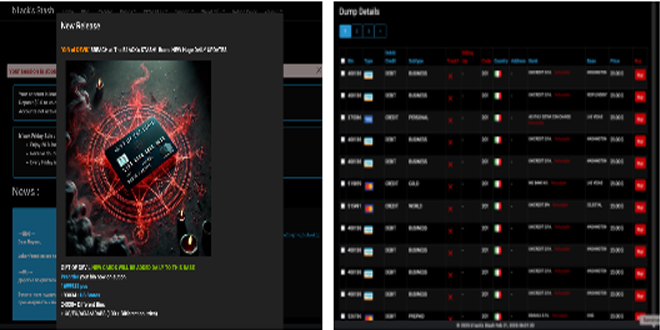
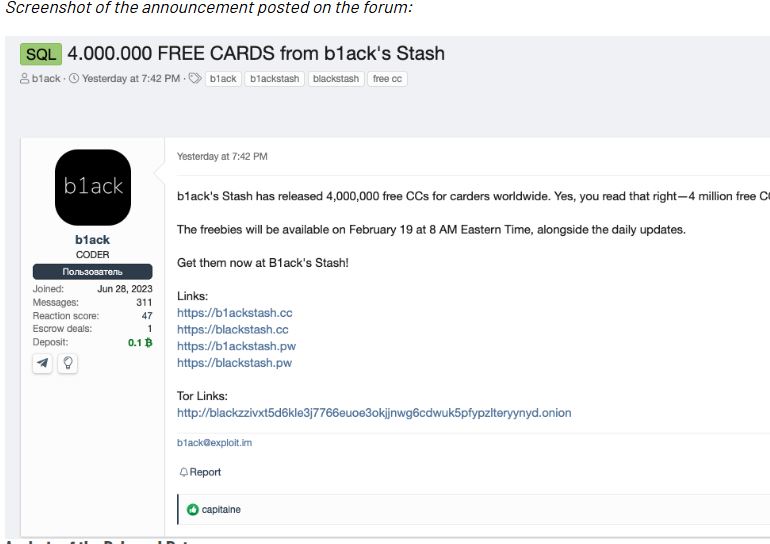
On February 19, 2025, the illegal marketplace B1ack’s Stash released over 1 million unique stolen credit and debit card details for free. This approach mirrors the strategy used by BidenCash, where criminals distribute stolen data widely to attract attention to their marketplace.
On February 17, a popular deep web forum announced the release of 4 million free credit cards. The upload included 6 archives containing 1,018,014 unique cards, with 192,174 issued by European banks.
Analysis of the Released Data:
The leaked data contains highly sensitive information, including:
Credit/debit card number, expiration date, CVV2, cardholder’s personal details (name, address, date of birth, phone number), email address, and IP address used in the transaction
Source of the Data Leak: Web Skimming
The analysis suggests that the data was likely stolen through Web Skimming, which involves adding malicious JavaScript to compromised e-commerce payment pages to capture sensitive user information in real-time.
User-Agent and IP address data suggest that a web skimmer was used to steal information.
Inside the B1ack’s Stash Marketplace:
The B1ack’s Stash marketplace used a free card release to attract new users. After this initial drop, additional cards were sold for about $25 each.
Cards are categorized as credit, debit, or prepaid, and sorted by country and bank. The dumps contain magnetic stripe data that criminals can use to create cloned cards.
Risks and Implications:
The public release of such detailed data significantly increases the risk of:
Financial fraud: Direct use of stolen cards for online purchases.
Identity theft: Personal data can be exploited for further illicit activities.
Targeted phishing: Email addresses and phone numbers can be used for sophisticated phishing campaigns.
Recommendations:
For financial institutions and end-users:
Banks and issuers should closely monitor compromised cards and quickly inform affected customers. Online merchants need to secure their payment systems against Web Skimmers. Users should regularly review their bank statements and report any suspicious activity right away.
This data breach shows the urgent need for proactive cybersecurity, especially in online payment systems. Web skimming is a major threat to e-commerce and credit card users.
Salt Typhoon Exploited CVE-2018-0171 to Target U.S. Telecom Networks
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind