Microsoft security experts recently conducted an exploration on how to effectively use Azure Logs to identify and counteract threat actions. Azure’s defense mechanism relies on effectively understanding and using logs to hunt for threats.
Microsoft focuses on integrating best practices for log management, analysis, and incident response to stay proactive against evolving cyber threats.
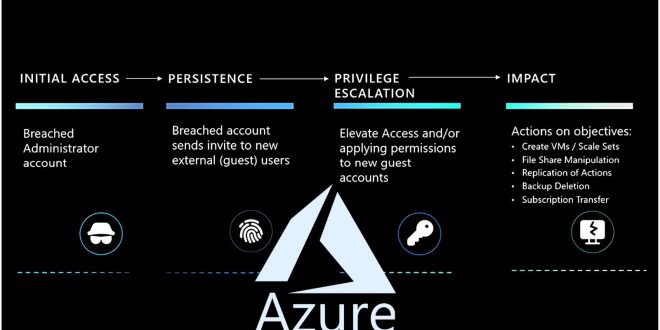
Identifying the initial breach and understanding subsequent actions is crucial in this process. Microsoft emphasizes the importance of integrating best practices for managing logs, analyzing them, and responding to incidents to stay ahead of cyber threats.
Microsoft describes a hypothetical attack scenario called “Pass the Cookie” where an attacker steals a user’s session cookie to gain unauthorized access to their account. It is important to closely monitor and analyze Azure logs to detect sophisticated attacks.
Log Analysis Techniques:
“To simplify cybersecurity challenges, Microsoft recommends utilizing Azure Log Analytics.” This tool is essential for investigating security incidents within Azure subscriptions.”
By sending both Microsoft Entra ID Audit logs and Azure Activity logs to Log Analytics, organizations can consolidate these logs in the CloudAppEvents table.

Simultaneously, Log Analytics organizes this data into the AuditLogs and AzureActivity tables.
Microsoft provides examples of Log Analytics queries, such as hunting for Azure Role assignments to newly added guest user accounts, demonstrating the practical application of log analysis in identifying potential security threats and vulnerabilities.
Understanding the scope and complexity of threat actor actions is crucial in fortifying defenses against cyberattacks. The detailed analysis of logs enables organizations to trace attackers’ steps, from the initial breach to their movements within the Azure environment. This insight is invaluable in developing strategies to prevent future attacks and enhance the security posture of cloud subscriptions.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind