AWS announced new security features at its re:Inforce conference, such as identity and malware protection services. The cloud giant added passkeys to the list of supported multi-factor authentication (MFA) mechanisms for root and Identity and Access Management (IAM) users.
The company also started enforcing MFA on root users, particularly AWS Organization management account users.
By F2
/ Tuesday , June 24 2025
The U.S. House of Representatives has banned congressional staff from using WhatsApp on government devices due to security concerns, as...
Read More
By F2
/ Tuesday , June 24 2025
Kaspersky found a new mobile malware dubbed SparkKitty in Google Play and Apple App Store apps, targeting Android and iOS....
Read More
By F2
/ Tuesday , June 24 2025
OWASP has released its AI Testing Guide, a framework to help organizations find and fix vulnerabilities specific to AI systems....
Read More
By F2
/ Tuesday , June 24 2025
In a major milestone for the country’s digital infrastructure, Axentec PLC has officially launched Axentec Cloud, Bangladesh’s first Tier-4 cloud...
Read More
By infosecbulletin
/ Monday , June 23 2025
A hacking group reportedly linked to Russian government has been discovered using a new phishing method that bypasses two-factor authentication...
Read More
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
“You can use the built-in authenticators in your phones and laptops to unlock a cryptographically secured credential to your AWS sign-in experience,” AWS said. “And when using a cloud service to store the passkey (such as iCloud keychain, Google accounts, or 1Password), the passkey can be accessed from any of your devices connected to your passkey provider account. This helps you to recover your passkey in the unfortunate case of losing a device.”
IAM Access Analyzer now has custom policy checks to detect policies that allow access to important AWS resources or grant public access. AWS has also introduced guided revocation in IAM Access Analyzer. This feature helps users by providing guidance on how to revoke unnecessary permissions that grant access.
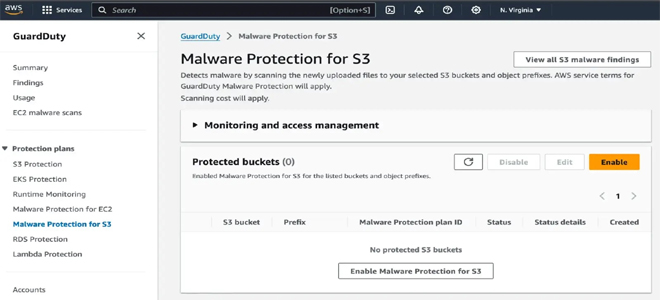
AWS announced that Amazon GuardDuty Malware Protection is now available for the Amazon S3 service. This feature allows users to detect malicious files in S3 buckets. Previously, GuardDuty Malware Protection only provided agentless scanning on Amazon EBS volumes attached to EC2 and container workloads.
The company introduced a new feature in AWS CloudTrail Lake. This feature uses gen-AI to help customers analyze CloudTrail logs for compliance, security, and operational needs.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind