BGD e-Gov Cert, the government’s cyber issue watchdog, has issued a warning about cyber attacks in the country. The agency released a report on Friday (April 21) called “Situational Alerts on Cyber Threats.”
The published report mentions measures to ensure cyber security of critical information infrastructure, banks, financial institutions, health care, government and private institutions.
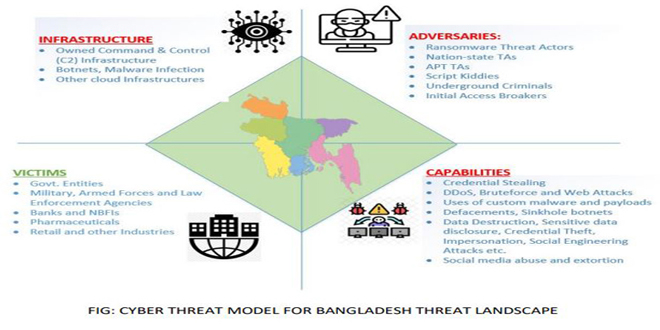
Published reports say that various ransomware groups attacked the country recently. Among these groups “money message group”and the Lockbit ransomware are the two.
Also worth mentioning APT groups are “Infy APT”, Infall APT”, “Emissary Panda”, “Threatneedle” and “Muddywater”. According to the report, in March 2023, the “Money Message Group” attacked an institution in the country.In addition, Lockbit ransomware attacked a large pharmaceutical company in Bangladesh this month.
In this regard, the project director of Cert Eng. Saiful Alam Khan told infosecbulletin.com, the country’s largest pharmaceutical company “Aristopharma was attacked by Lockbit ransomware in April 2023.
CII-affiliated company Biman Bangladesh informed us at the time of their incident and worked in collaboration with both, but the pharmaceutical company did not inform CERT about the cyber attack, so CERT is not aware of the cyber attack damage or next steps.
Saiful Islam said, we have to come out of this kind of trend. Reporting incidents can lead to quick action to reduce risk and avoid major losses.
Apart from this, criminals have also carried out “web defacement” attacks in the country using web shell injection method. During regular monitoring of CERT, the activities of “Infi APT”, Infall APT”, “Emissary Panda”, “Threatneedle”, “Muddywater”, “Tick” and “Machit” APT have been observed in the country.
CERT has announced a series of measures to keep the institutions safe from attacks and damage:
- 24/7 network monitoring should be done especially after scheduled office hours.
- It is important to pay special attention to the services like DNS, NTP, network middleboxes, they should be configured correctly on the Internet so that no credentials are spread in any way.
VAPT (Vulnerability Assessment and Penetration Testing) of all systems should be ensured regularly.
- CERT focuses on configuring web applications according to Owasp’s guidelines.
Besides, the report mentions to ensure adequate controls on “need to know” basis.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind