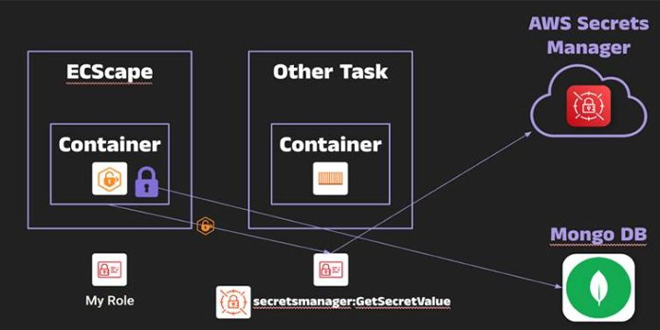
Security researchers disclosed a cirtical flaw in Amazon Elastic Container Service (ECS) that enables harmful containers to steal AWS credentials from other tasks on the same EC2 instance.
The attack, dubbed “ECScape,” exploits an undocumented internal protocol to impersonate the ECS agent and harvest privileged credentials without requiring container breakout.
By infosecbulletin
/ Tuesday , August 12 2025
In early August 2025, cybersecurity teams in Türkiye detected a new Java-based loader that avoided detection by all public sandboxes,...
Read More
By infosecbulletin
/ Monday , August 11 2025
ESET researchers found a zero-day vulnerability in WinRAR for Windows, tracked as CVE-2025-8088, which has been used to run malicious...
Read More
By infosecbulletin
/ Sunday , August 10 2025
A sophisticated cyber fraud has stolen over ₹5.58 crore from many bank accounts, highlighting serious concerns about digital payment security....
Read More
By infosecbulletin
/ Sunday , August 10 2025
Google confirmed that a recent data breach in one of its Salesforce CRM systems exposed information about potential Google Ads...
Read More
By infosecbulletin
/ Saturday , August 9 2025
More than 28,000 unpatched Microsoft Exchange servers are publicly accessible and vulnerable to the critical security flaw CVE-2025-53786, as reported...
Read More
By infosecbulletin
/ Saturday , August 9 2025
Google has unveiled its best practices aimed at thwarting dangling bucket takeovers, encouraging developers to fortify their cloud environments. The...
Read More
By infosecbulletin
/ Saturday , August 9 2025
Researchers revealed critical zero-day vulnerabilities that bypass Windows BitLocker encryption, enabling attackers with physical access to quickly extract data from...
Read More
By infosecbulletin
/ Friday , August 8 2025
Security researchers disclosed a cirtical flaw in Amazon Elastic Container Service (ECS) that enables harmful containers to steal AWS credentials...
Read More
By infosecbulletin
/ Friday , August 8 2025
Let’s look at 7 tools for automating patch deployment. Each tool offers unique features for various environments, from small DevOps...
Read More
By infosecbulletin
/ Friday , August 8 2025
Germany's top court ruled on Thursday that police can secretly install spy software on phones and computers only for serious...
Read More

Vulnerability Overview:
The ECScape attack takes advantage of a basic mistake in how ECS handles IAM credentials on shared EC2 instances.
Running multiple containers with varying privilege levels on the same host can lead to security risks. A low-privileged container could exploit the ECS Agent Communication Service (ACS) protocol to access credentials from higher-privileged tasks.
The vulnerability was discovered by security researcher Naor Haziz during development of an eBPF-based monitoring tool.
While investigating how ECS tasks retrieve metadata, Haziz observed that the ECS agent receives task credentials via a WebSocket connection to AWS’s control plane with a suspicious “sendCredentials=true” parameter.
AWS advises ECS users to take protective measures. Key strategies include not deploying high-privilege tasks with untrusted containers on shared instances, using dedicated hosts for critical services, or switching to AWS Fargate for isolated task environments.
Additional protections involve restricting IMDS access through the ECS_AWSVPC_BLOCK_IMDS setting, enforcing IMDSv2, and implementing least-privilege IAM policies.
Organizations should remove unnecessary Linux capabilities to reduce post-compromise risks.
The disclosure emphasizes key security aspects of container orchestration platforms and the need to grasp isolation boundaries in cloud environments.
While AWS has not indicated plans to modify the underlying architecture, the research emphasizes why Fargate’s micro-VM isolation provides stronger security guarantees for sensitive workloads.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind