Millions of software repositories on GitHub are likely vulnerable to an attack called RepoJacking, a new study has revealed.
This includes repositories from organizations such as Google, Lyft, and several others, Massachusetts-based cloud-native security firm Aqua said in a Wednesday report.
The supply chain vulnerability, also known as dependency repository hijacking, is a class of attacks that makes it possible to take over retired organizations or user names and publish trojanized versions of repositories to run malicious code.
“When a repository owner changes their username, a link is created between the old name and the new name for anyone who downloads dependencies from the old repository,” researchers Ilay Goldman and Yakir Kadkoda said. “However, it is possible for anyone to create the old username and break this link.”
Alternatively, a similar scenario could arise when a repository ownership is transferred to another user and the original account is deleted, thus allowing a bad actor to create an account with the old username.
Aqua said a threat actor could leverage websites like GHTorrent to extract GitHub metadata associated with any public commits and pull requests to compile a list of unique repositories.
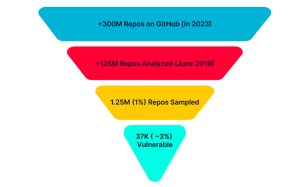
An analysis of a subset of 1.25 million repositories for the month of June 2019 revealed that as many as 36,983 repositories were vulnerable to RepoJacking, denoting a 2.95% success rate.
With GitHub containing more than 330 million repositories, the findings suggest that millions of repositories could be vulnerable to a similar attack.
One such repository is google/mathsteps, which was previously under the ownership of Socratic (socraticorg/mathsteps), a company that was acquired by Google in 2018.
“When you access https://github.com/socraticorg/mathsteps, you are being redirected to https://github.com/google/mathsteps so eventually the user will fetch Google’s repository,” the researchers said.
“However, because the socraticorg organization was available, an attacker could open the socraticorg/mathsteps repository and users following Google’s instructions will clone the attacker’s repository instead. And because of the npm install this will lead to arbitrary code execution on the users.”
This is not the first time such concerns have been raised. In October 2022, GitHub moved to close a security loophole that could have been exploited to create malicious repositories and mount supply chain attacks by circumventing popular repository namespace retirement.
To mitigate such risks, it’s recommended that users periodically inspect their code for links that may be retrieving resources from external GitHub repositories.
“If you change your organization name, ensure that you still own the previous name as well, even as a placeholder, to prevent attackers from creating it,” the researchers said.
Source: hackernews/security firm Aqua
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














