Telegram is one of the most popular social media platforms in the world. The platform is constantly being updated. But recently cyber security experts have discovered a new malware. The malicious ‘WhatsApp Spy Mode’ has already attacked messaging platform Telegram users at least 340 thousand times.
According to the researchers, this happened throughout the month of October. A report about this terrible malware has come to light. According to cybersecurity firm Kaspersky, the malware mainly attacks people who speak Arabic, Azeri languages.
By infosecbulletin
/ Monday , May 12 2025
Google will pay about $1.4 billion to Texas to settle two lawsuits regarding location tracking and biometric data storage without...
Read More
By infosecbulletin
/ Friday , May 9 2025
YouTube has restricted access to at least four Bangladeshi television channels in India following a takedown request from the Indian...
Read More
By infosecbulletin
/ Friday , May 9 2025
Microsoft has fixed critical vulnerabilities in its core cloud services, including Azure Automation, Azure Storage, Azure DevOps, and Microsoft Power...
Read More
By infosecbulletin
/ Thursday , May 8 2025
The cyber threat landscape is rapidly changing, with a notable increase in ransomware activity in April 2025, driven by the...
Read More
By infosecbulletin
/ Thursday , May 8 2025
SonicWall has released patches for three security flaws in SMA 100 Secure Mobile Access appliances that could allow remote code...
Read More
By infosecbulletin
/ Thursday , May 8 2025
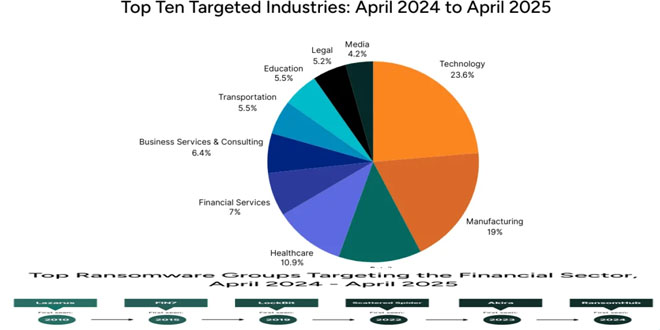
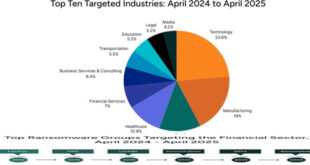
From April 2024 to April 2025, Flashpoint analysts noted that the financial sector was a major target for threat actors,...
Read More
By infosecbulletin
/ Thursday , May 8 2025
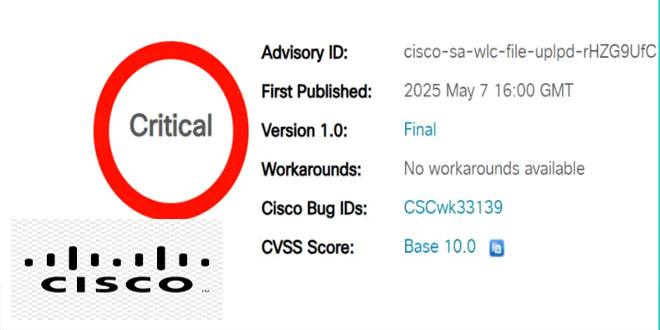
Cisco has issued a security advisory for a critical vulnerability in its IOS XE Software for Wireless LAN Controllers (WLCs)....
Read More
By infosecbulletin
/ Wednesday , May 7 2025
Attackers linked to the Play ransomware operation deployed a zero-day privilege escalation exploit during an attempted attack against an organization...
Read More
By infosecbulletin
/ Wednesday , May 7 2025
Hackers are exploiting an unauthenticated remote code execution vulnerability in the Samsung MagicINFO 9 Server to take control of devices...
Read More
By infosecbulletin
/ Tuesday , May 6 2025
CISA added the Langflow vulnerability, CVE-2025-3248 (CVSS score 9.8), to its Known Exploited Vulnerabilities catalog. Langflow is a popular tool...
Read More
Users who crave additional features from popular messaging apps often take the help of third-party apps. This is where the danger lies, the researchers explained. Third party apps offer additional features. But it also contains some malware.
While this new WhatsApp mod offers scheduled messages and customizable options, it also contains malicious spyware, they said. Victim contact and account details are sent every 5 minutes. At the same time, this spy module is also able to set up microphone recording and extract files from external storage.
The manifest file of the modified WhatsApp client contains several suspicious elements, which are not present in the original version. Whenever the receiver starts a service, the spy module is also activated when the phone is turned on or while charging. And once that spy module is activated, the malicious implant sends a request with device information to the attacker’s server. The data that is covered includes IMEI, phone number, country and network codes, among others.
However, users from Azerbaijan, Saudi Arabia, Yemen, Turkey and Egypt are the most affected. As the target is Arabic and Azerbaijani speakers, people from USA, Russia, Britain, Germany and other countries are also affected by this scam. Experts advise to be careful in using social media.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind