The Cyber Threat Intelligence team of BGD e-GOV CIRT has issued a warning about ongoing attacks using two zero-day vulnerabilities in Cisco’s IOS XE Software web UI feature. Successful exploitation attempts have been observed against organizations in Bangladesh. This advisory is intended for IT teams responsible for configuring and managing routers and network switches in their organizations.
1. CVE-2023-20198 (Critical | CVSS: 10.0): Remote attackers can create local user accounts, which poses a serious risk of privilege escalation.
2. CVE-2023-20273 (Medium | CVSS: 7.2): It allows for higher privileges and injection of malicious implants, in addition to the initial vulnerability.
Scope & Impact:
Affected Systems: All Cisco IOS XE Software with Web UI enabled.
Risk Level: Critical
Potential Impact:
Unauthorized intruders are redirecting and injecting implants, causing security breaches in network traffic.
Recommendations
To determine if a device might be compromised, consider the following actions:
1. Examine Log Messages:
Review system logs for specific log entries involving unfamiliar local users, including:
* %SYS-5-CONFIG_P: Configuration modifications made by certain processes as “user.”
* %SEC_LOGIN-5-WEBLOGIN_SUCCESS: Records of successful web logins, including user and
source IP details.
* %WEBUI-6-INSTALL_OPERATION_INFO: Instances of user-initiated installations for unknown
filenames.
2. Detect Malicious Implant:
To detect a malicious implant on possibly compromised Cisco IOS XE devices, use the following command: replace “DEVICEIP” with the IP address of the device you want to target.
Use a curl command to find systems that have known implant variants without activating the implant’s main functions. You can use %25 (percent-encoded percent) to get different responses. If the response includes a 404 HTTP error and a “404 Not Found” message, it indicates a recognized implant variation. Systems without the implant will either give a normal 404 HTTP response or a JavaScript redirect with a 200 HTTP response.
If the implant is present, you will get a response similar to the following:
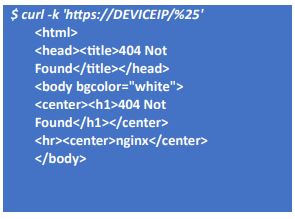
If the implant is not present, you will get a different response. For example:
![]()
$ curl -k ‘https://DEVICEIP/%25′
<script>window.onload=function(){ url =’/webui’;window.location.href=url;}</script>
Please note:
When inspecting devices with insecure web interfaces, apply the HTTP scheme.

Mitigations
Cisco has released software updates to fix the vulnerabilities mentioned in this advisory. Customers with service agreements can get the security patches through their usual update sources. More information can be found in the Cisco advisory at this link:
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosx
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind