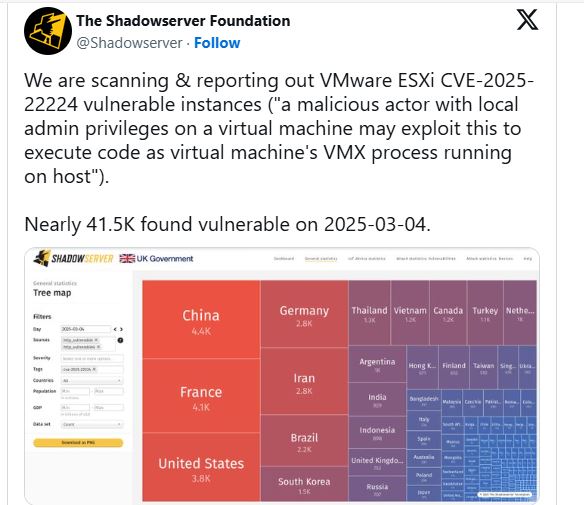
As of March 4, 2025, Shadowserver found that over 41,500 internet-exposed VMware ESXi hypervisors are vulnerable to the actively exploited CVE-2025-22224.
By F2
/ Tuesday , June 24 2025
OWASP has released its AI Testing Guide, a framework to help organizations find and fix vulnerabilities specific to AI systems....
Read More
By F2
/ Tuesday , June 24 2025
In a major milestone for the country’s digital infrastructure, Axentec PLC has officially launched Axentec Cloud, Bangladesh’s first Tier-4 cloud...
Read More
By infosecbulletin
/ Monday , June 23 2025
A hacking group reportedly linked to Russian government has been discovered using a new phishing method that bypasses two-factor authentication...
Read More
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
By infosecbulletin
/ Sunday , June 15 2025
WestJet, Canada's second-largest airline, is looking into a cyberattack that has affected some internal systems during its response to the...
Read More
By infosecbulletin
/ Saturday , June 14 2025
Resecurity found 7.4 million records of Paraguayan citizens' personal information leaked on the dark web today. Last week, cybercriminals attempted...
Read More
41,500 unpatched ESXi instances represent a major part of global virtualization, especially in healthcare, finance, and telecommunications.
Broadcom released an emergency update to fix a vulnerability that allows attackers with local admin access to a virtual machine (VM) to run malicious code on the hypervisor, posing serious risks to cloud infrastructure and enterprise networks.
Hypervisor Escape via TOCTOU Flaw:
CVE-2025-22224 (CVSS 9.3) is a TOCTOU vulnerability found in VMware ESXi and Workstation. It lets attackers cause an out-of-bounds write in the VMX process, which manages individual VMs.
Exploitation occurs when an attacker gains administrative access to a virtual machine’s guest operating system, allowing them to escalate privileges to the host system. This gives them complete control over all virtual machines on the hypervisor, data stores, and connected networks.
The Microsoft Threat Intelligence Center found vulnerabilities and informed Broadcom, highlighting their use in ransomware and APT campaigns. The U.S. CISA added CVE-2025-22224 to its Known Exploited Vulnerabilities list on March 4, requiring federal agencies to fix it by March 25, 2025.
Mitigations:
Broadcom released patches for all affected products, including:
VMware ESXi 8.0: Update to ESXi80U3d-24585383 or ESXi80U2d-24585300
VMware ESXi 7.0: Update to ESXi70U3s-24585291
VMware Cloud Foundation 5.x/4.5.x: Apply async patches detailed in KB389385.
Organizations should quickly isolate ESXi management interfaces from the internet, review VM administrative access, and monitor unusual VMX activity. Rapid7 and Tenable have added detection checks in their platforms to find exposed systems.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














