A secretive cyber attack known as Gelsemium, which lasted for six months from 2022 to 2023, targeted a government in Southeast Asia. The cyberespionage group known as Gelsemium has been actively operating since 2014, with a focus on targeting government institutions, educational organizations, and electronic manufacturers in East Asia and the Middle East.
ESET’s 2021 report describes the threat group as “quiet,” highlighting their extensive technical skills and programming knowledge that have allowed them to avoid detection for a long time. A recent report from Palo Alto Network’s Unit 42 shows that a new Gelsemium campaign is using backdoors that are not commonly seen. These backdoors are connected to threat actors with moderate confidence.
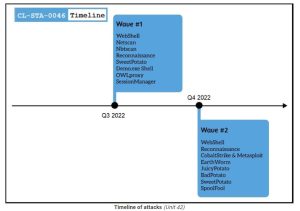
Recent Gelsemium attacks
Gelsemium successfully initiated its first attack by installing web shells, possibly by exploiting vulnerabilities in servers exposed to the internet. Unit 42 has identified the presence of web shells known as ‘reGeorg,’ ‘China Chopper,’ and ‘AspxSpy.’ These web shells are widely accessible and utilized by various threat groups, posing a challenge when it comes to attribution.
Gelsemium leveraged the power of web shells to carry out essential network reconnaissance, expertly maneuver through SMB, and skillfully retrieve additional payloads. There are several powerful tools that can assist in lateral movement, data collection, and privilege escalation. These include OwlProxy, SessionManager, Cobalt Strike, SpoolFool, and EarthWorm.
Cobalt Strike is an extensively employed suite for penetration testing, EarthWorm serves as a readily accessible SOCKS tunneler, and SpoolFool stands as an open-source tool for local privilege escalation. Therefore, it is important to note that these three resources, though not exclusive to Gelsemium, are highly valuable in their own right.
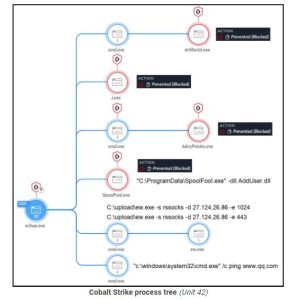
According to Unit 42, the OwlProxy is an exceptional and specialized HTTP proxy and backdoor tool. It has been reported by Unit 42 that Gelsemium used this tool in a previous attack aimed at the Taiwanese government.
In the latest campaign, the attacker placed a file (wmipd.dll) on the compromised system’s disk and created a service to run it.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














