Pwn2Own Vancouver 2024 hacking competition is over. Hackers earned $1,132,500 for showing 29 unique zero-days.
Participants in the Pwn2Own Vancouver 2024 hacking competition earned $1,132,500 for demonstrating 29 unique zero-days. On the first day, Team Synacktiv successfully demonstrated exploits against a Tesla car.
By F2
/ Tuesday , June 24 2025
The U.S. House of Representatives has banned congressional staff from using WhatsApp on government devices due to security concerns, as...
Read More
By F2
/ Tuesday , June 24 2025
Kaspersky found a new mobile malware dubbed SparkKitty in Google Play and Apple App Store apps, targeting Android and iOS....
Read More
By F2
/ Tuesday , June 24 2025
OWASP has released its AI Testing Guide, a framework to help organizations find and fix vulnerabilities specific to AI systems....
Read More
By F2
/ Tuesday , June 24 2025
In a major milestone for the country’s digital infrastructure, Axentec PLC has officially launched Axentec Cloud, Bangladesh’s first Tier-4 cloud...
Read More
By infosecbulletin
/ Monday , June 23 2025
A hacking group reportedly linked to Russian government has been discovered using a new phishing method that bypasses two-factor authentication...
Read More
By infosecbulletin
/ Wednesday , June 18 2025
Russian cybersecurity experts discovered the first local data theft attacks using a modified version of legitimate near field communication (NFC)...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
Cybersecurity researcher Jeremiah Fowler discovered an unsecured database with 170,360 records belonging to a real estate company. It contained personal...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
GreyNoise found attempts to exploit CVE-2023-28771, a vulnerability in Zyxel's IKE affecting UDP port 500. The attack centers around CVE-2023-28771,...
Read More
By infosecbulletin
/ Tuesday , June 17 2025
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently included two high-risk vulnerabilities in its Known Exploited Vulnerabilities (KEV)...
Read More
By infosecbulletin
/ Monday , June 16 2025
SafetyDetectives’ Cybersecurity Team discovered a public post on a clear web forum in which a threat actor claimed to have...
Read More
The researcher Manfred Paul (@_manfp) won the Master of Pwn earning $202,500 and 25 points.
Participants demonstrated several zero-day exploits against various products such as Apple Safari, Google Chrome, and Microsoft Edge browsers, Windows 11, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, and Tesla. On Day Two, Manfred Paul (@_manfp) managed to escape the sandbox in Mozilla Firefox by exploiting an OOB Write for the RCE and an exposed dangerous function bug. He was rewarded with $100,000 and 10 Master of Pwn points for this successful hack.
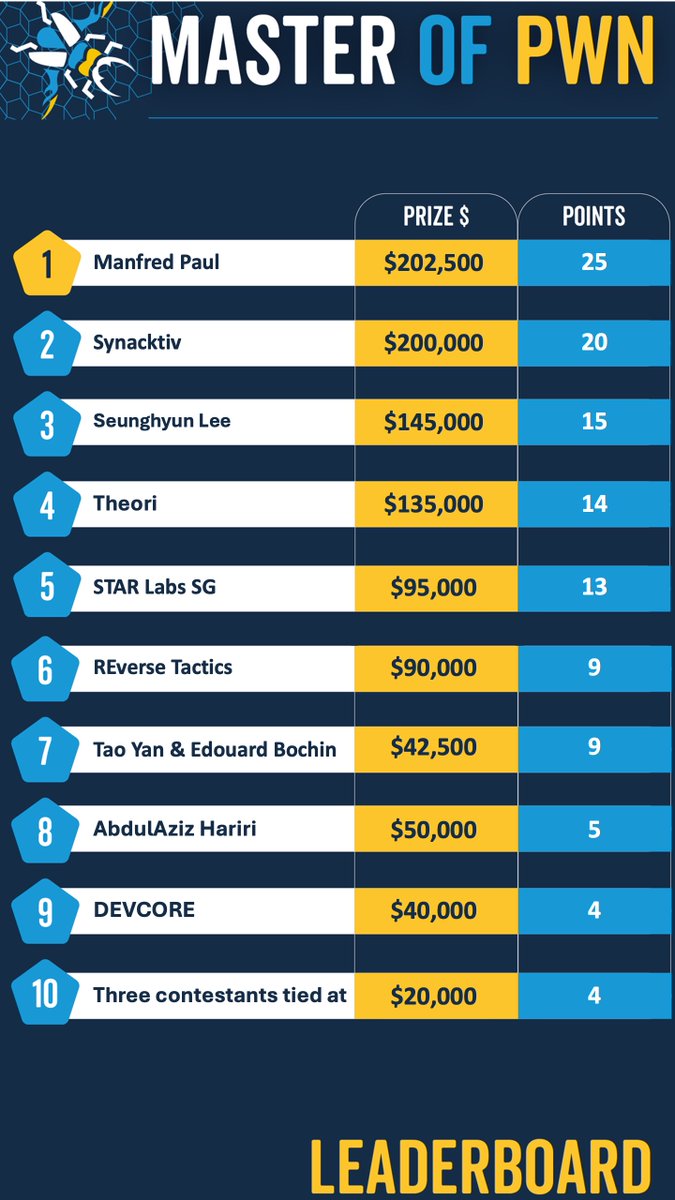
Seunghyun Lee, a researcher from KAIST Hacking Lab, used a UAF to remotely execute code in Microsoft Edge and Google Chrome. He earned $85,000 and 9 Master of Pwn points.
The STAR Labs SG team showed the first Docker desktop escape at the Pwn2Own hacking competition by using two vulnerabilities, including a UAF. They won $60,000 and 6 Master of Pwn points.
The complete list of results for the first Two of the Pwn2Own Vancouver 2024 hacking competition is available here:
https://www.zerodayinitiative.com/blog/2024/3/21/pwn2own-vancouver-2024-day-two-results
Vendors have 90 days to fix the vulnerabilities found during the Pwn2Own hacking competition before they are publicly disclosed by TrendMicro’s Zero Day Initiative.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














