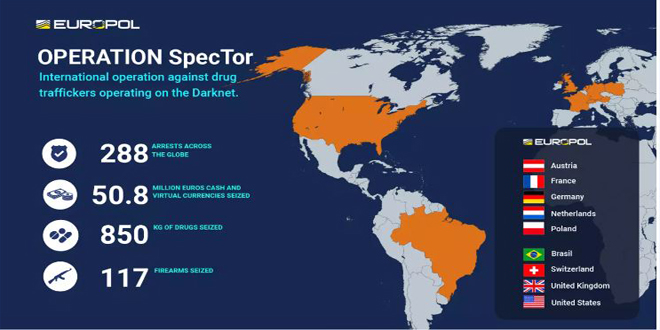
In an operation coordinated by Europol and involving nine countries, law enforcement have seized the illegal dark web marketplace “Monopoly Market” and arrested 288 suspects involved in buying or selling drugs on the dark web. More than EUR 50.8 million (USD 53.4 million) in cash and virtual currencies, 850 kg of drugs, and 117 firearms were seized. The seized drugs include over 258 kg of amphetamines, 43 kg of cocaine, 43 kg of MDMA and over 10 kg of LSD and ecstasy pills.
This operation, codenamed SpecTor, was composed of a series of separate complementary actions in Austria, France, Germany, the Netherlands, Poland, Brazil, the United Kingdom, the United States, and Switzerland.
Intelligence packages as basis for investigations
Europol has been compiling intelligence packages based on troves of evidence provided by German authorities, who successfully seized the marketplace’s criminal infrastructure in December 2021. These target packages, created by cross-matching and analysing the collected data and evidence, served as the basis for hundreds of national investigations. The vendors arrested as a result of the police action against Monopoly Market were also active on other illicit marketplaces, further impeding the trade of drugs and illicit goods on the dark web. As a result, 288 vendors and buyers who engaged in tens of thousands of sales of illicit goods were arrested across Europe, the United States and Brazil. A number of these suspects were considered high-value targets by Europol.
The arrests took place in the United States (153), the United Kingdom (55), Germany (52), the Netherlands (10), Austria (9), France (5), Switzerland (2), Poland (1) and Brazil (1). A number of investigations to identify additional individuals behind dark web accounts are still ongoing. As law enforcement authorities gained access to the vendors’ extensive buyer lists, thousands of customers across the globe are now at risk of prosecution as well.
Illicit marketplaces on the dark web
In the run-up to this coordinated operation, German and U.S. authorities also shut down ‘Hydra’, which was the highest-grossing dark web market with an estimated revenue of EUR 1.23 billion, in April 2022. The Hydra takedown saw EUR 23 million in cryptocurrencies seized by German authorities.
In terms of arrests, the operation was even more successful than previous operations codenamed DisrupTor (2020) with 179 and Dark HunTor (2021) with 150 arrests. It shows once more that international collaboration between police authorities is key for combatting crime on the Dark Web.
Commenting on Operation SpecTor, Europol’s Executive Director, Catherine De Bolle, said:
Our coalition of law enforcement authorities across three continents proves that we all do better when we work together. This operation sends a strong message to criminals on the dark web: international law enforcement has the means and the ability to identify and hold you accountable for your illegal activities, even on the dark web.
Europol‘s role
Europol’s European Cybercrime Centre facilitated the information exchange in the framework of the Joint Cybercrime Action Taskforce (J-CAT) hosted at the Europol headquarters in The Hague, the Netherlands. After cross-checking evidence through the Europol databases, Europol analysts prepared target packages and cross-matched reports containing valuable data to identify vendors on the dark web. Europol also coordinated the international law enforcement action.
Headquartered in The Hague, the Netherlands, Europol supports the 27 EU Member States in their fight against terrorism, cybercrime and other serious and organised forms of crime. We also work with many non-EU partner states and international organisations. From its various threat assessments to its intelligence-gathering and operational activities, Europol has the tools and resources it needs to do its part in making Europe safer.
Authorities taking part in Operation SpecTor:
- Austria: Criminal Intelligence Service Austria with various Provincial Criminal Police Departments (Bundeskriminalamt und Landeskriminalämter)
- France: French Customs (Douane)
- Germany: Federal Criminal Police Office (Bundeskriminalamt), Central Criminal Investigation Department of Oldenburg (Zentrale Kriminalinspektion Oldenburg), General Prosecutor’s Office in Frankfurt/Main – Cybercrime Center (Generalstaatsanwaltschaft Frankfurt/Main, Zentralstelle zur Bekämpfung der Internetkriminalität), Berlin Police (Polizei Berlin), various police departments (Dienststellen der Länderpolizeien), German Customs Investigation (Zollfahndungsämter)
- Netherlands: National Police (Politie)
- Poland: Central Cybercrime Bureau (Centralne Biuro Zwalczania Cyberprzestępczości)
- Brazil: Civil Police of the State of Piauí (Polícia Civil do Estado do Piauí), Civil Police of the Federal District (Polícia Civil do Distrito Federal), National Secretariat of Public Security – Directorate of Integrated Operations and Intelligence – Cyber Operations Laboratory (Laboratório de Operações Cibernéticas da Diretoria de Operações Integradas e de Inteligência – Secretaria Nacional de Segurança Pública)
- Switzerland: Zurich Cantonal Police (Kantonspolizei Zürich) and Public Prosecutor’s Office II of the Canton of Zurich (Staatsanwaltschaft II)
- United Kingdom: National Crime Agency (NCA), National Police Chiefs’ Council (NPCC)
- United States: The Department of Justice (DOJ), Federal Bureau of Investigation (FBI), U.S. Drug Enforcement Administration (DEA), U.S. Postal Inspection Service (USPIS), U.S. Immigration and Customs Enforcement (ICE)’s Homeland Security Investigations (HSI), U.S. Customs and Border Protection (CBP), Financial Crimes Enforcement Network (FinCEN), Bureau of Alcohol, Tobacco, and Firearms (ATF), Naval Criminal Investigative Service (NCIS), Department of Defense (DOD), U.S. Food and Drug Administration (FDA) Office of Criminal Investigations, Internal Revenue Service Criminal Investigation (IRS-CI)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind