According to Shadowserver Foundation around 17,000 Fortinet devices worldwide have been compromised using a new technique called “symlink”. This number has increased from the initial 14,000 and is expected to rise as investigations continue.
The attack takes advantage of known vulnerabilities in Fortinet’s FortiGate devices. After gaining access, the threat actors created a symbolic link (symlink) that connected the user filesystem to the root filesystem in a folder for SSL-VPN language files.
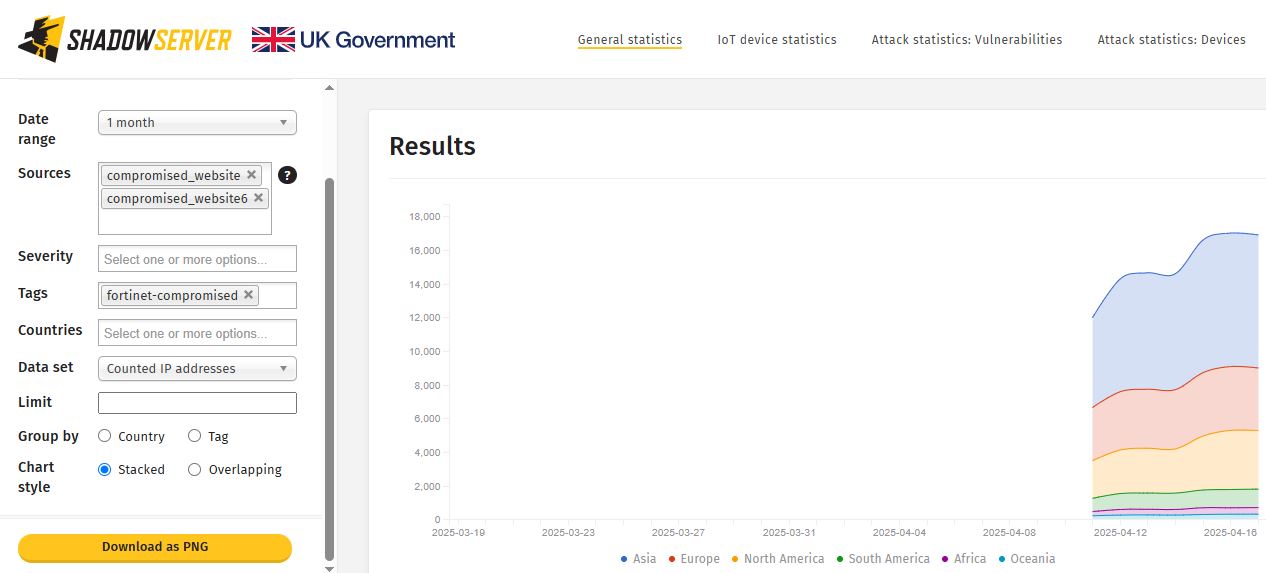
The graph shows a rapid increase in compromised Fortinet devices in various regions from April 11 to April 16, 2025.
Cybersecuritynews reported, “Asia is the most heavily impacted, accounting for roughly half of the total cases, followed by Europe and North America, which together represent a significant portion of the affected devices. South America, Africa, and Oceania show much smaller numbers in comparison”.
The number of affected devices has exceeded 17,009, with most of the increase happening in just a few days.
BleepingComputer reported, Last week, Fortinet warned customers that they had discovered a new persistence mechanism used by a threat actor to retain read-only remote access to files in the root filesystem of previously compromised but now patched FortiGate devices.
“A threat actor used a known vulnerability to implement read-only access to vulnerable FortiGate devices. This was achieved via creating a symbolic link connecting the user filesystem and the root filesystem in a folder used to serve language files for the SSL-VPN. This modification took place in the user filesystem and avoided detection,” Fortinet said.
Fortinet has issued an updated AV/IPS signature to identify and eliminate a malicious symbolic link on compromised devices. The latest firmware version also detects and removes this link, while preventing unknown files and folders from being accessed through the built-in web server.

Accroding to SocRadar, The technique used in this case involves a symbolic link, commonly referred to as a “symlink.” A symlink is a type of file system pointer that functions much like a shortcut, redirecting access from one file location to another.
“Based on telemetry from The Shadowserver Foundation, the number of compromised devices has surpassed 17,000. These affected systems span multiple industries and geographies, indicating a broad and opportunistic campaign rather than one that is narrowly targeted”.
CISA warns of increasing risk tied to Oracle legacy Cloud leak
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














