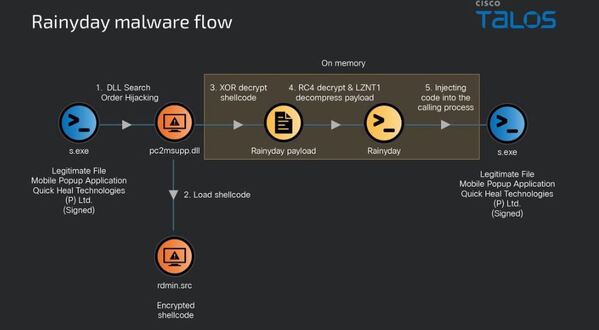
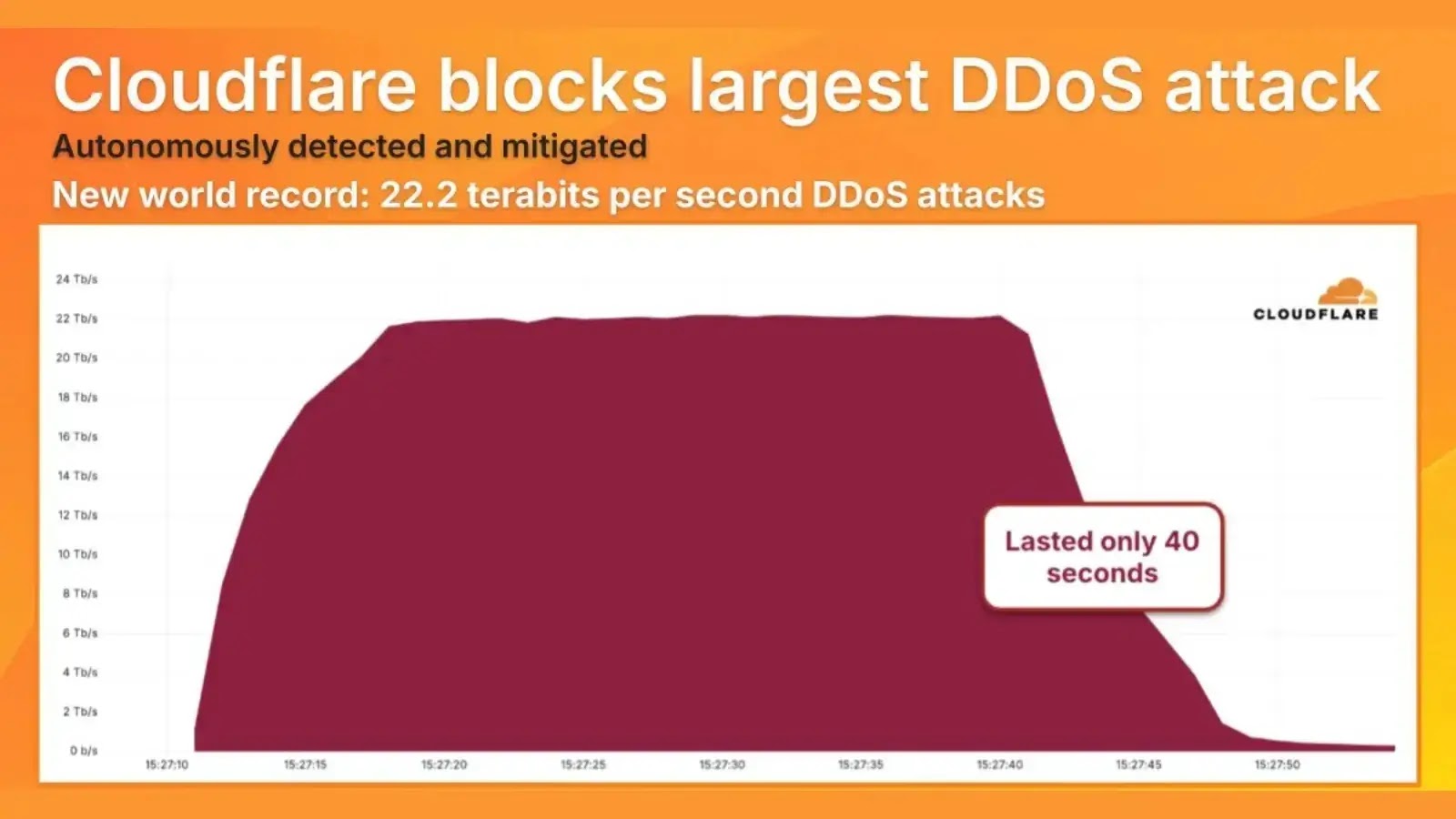
Cybersecurity is a constantly changing landscape; as technology advances and cyber criminals create new methods, the prevailing trends quickly alter. Here are some key cybersecurity trends to keep an eye on in 2024:
1. AI-driven attacks:
The role of Artificial Intelligence in the digital world is two-fold. While it has enabled us to develop systems capable of processing and analyzing data at unprecedented speed and precision, it has also equipped cybercriminals with the means to craft more advanced and focused attacks. It is crucial to allocate resources to AI-enabled defense mechanisms that foresee and nullify these threats before they inflict damage.
2. Sophisticated disinformation campaigns:
Disseminating misleading information has always been challenging, but the advent of the digital era has magnified its effects. It is feasible to produce and circulate false information globally, which can have far-reaching and destructive implications. To counter this, it is essential to create and apply advanced tools for detection and verification and foster media literacy and critical thinking abilities among the public.
3. Deepfakes:
The generation of synthetic media via AI has ushered in a new era of disinformation. Deepfakes can produce realistic photos, videos, and audio recordings of individuals saying or doing things they never actually said or did. To defend against this, we must invest in sophisticated detection tools and raise public awareness about the potential hazards of deepfakes.
4. Endpoint Detection and Response (EDR):
The surge in remote work and the increase in devices accessing corporate networks have made endpoints (devices like laptops, mobile phones, and tablets) a key target for cybercriminals. EDR solutions continuously monitor and analyze endpoint data to detect, investigate, and respond to cybersecurity threats in real time. EDR solutions can help organizations protect against advanced threats and enhance their security.
5. Ransomware:
Ransomware attacks involve encrypting a victim’s data and demanding a ransom for release. These attacks have grown increasingly expensive and disruptive. Establishing robust backup and recovery systems and educating employees about the dangers of phishing emails and other standard attack methods is essential.
6. Supply chain attacks:
Cybercriminals are targeting software vendors and their suppliers more frequently to gain access to their systems and data. This can lead to a series of compromises affecting multiple organizations. It is crucial for organizations to thoroughly assess their suppliers and implement robust security measures throughout the supply chain to reduce this risk.
7. Cloud security:
As organizations transition their operations to the cloud, it becomes a prime target for cyberattacks. Implementing robust cloud security measures, including multi-factor authentication, encryption, and regular security audits, is essential to safeguard our cloud assets.
8. IoT security:
The Internet of Things (IoT) connects billions of devices globally, opening up new possibilities for innovation and efficiency. However, many IoT devices lack adequate security, making them easy targets for cybercriminals. Implementing strong security measures at every stage of the IoT ecosystem, from device manufacture to network communication, is essential for protection.
9. 5G Network Risks:
The deployment of 5G networks promises faster internet speeds and the enablement of new technologies. However, it also introduces new security challenges. To protect against these risks, it is necessary to implement robust encryption, authentication, and network segmentation measures.
10. Mobile is the New Target:
As mobile devices become more widespread, they have become a key target for cyberattacks. Implementing robust mobile security measures, including regular software updates, strong passwords, and multi-factor authentication, is essential for protection.
11. Automotive Hacking:
Modern vehicles contain various electronic systems that enhance safety and convenience. However, these systems also present new opportunities for cybercriminals. Implementing strong security measures at every stage of the vehicle’s lifecycle, from design to manufacture to operation, is crucial.
12. Targeted attacks enhanced by smart device data:
The proliferation of smart devices has created a wealth of data for cybercriminals. To protect against this, we must secure our devices with strong passwords, regularly update our software, and exercise caution about the data we share online.
13. Exploited legacy systems in cyber-physical ecosystems:
Many organizations still rely on legacy systems not designed with modern security threats in mind. Updating or replacing these systems and implementing strong security measures to protect against potential vulnerabilities is essential.
14. Zero trust:
The traditional approach to cybersecurity, which assumes that everything inside the network can be trusted, must be reevaluated. Instead, it is necessary to adopt a zero-trust approach, which requires all users and devices to authenticate and authorize themselves before accessing resources.
15. Human-centric design:
Centering the human element in our cybersecurity efforts can reduce operational friction and increase control adoption. This involves designing systems that are intuitive and user-friendly while providing strong security.
16. Human error:
Despite our best efforts, human error remains a significant cybersecurity risk. To mitigate this risk, comprehensive security awareness training for all employees is essential, along with implementing security policies and procedures that help minimize potential mistakes.
17. Privacy regulation:
As governments worldwide implement stricter privacy regulations, organizations must take steps to ensure compliance. This involves regularly reviewing and updating our data handling practices and implementing strong security measures to protect customer data.
18. Cyber risk quantification:
Quantifying cyber risk is crucial for making informed decisions about where to invest our cybersecurity resources. However, this is a complex task that many organizations struggle with. Investing in advanced analytics tools and developing a comprehensive understanding of our risk landscape is essential for improving our cyber risk quantification efforts.
19. Digital surveillance authoritarianism/loss of privacy:
As digital surveillance becomes more widespread, there is growing concern about the loss of privacy. To protect against this, it is essential to exercise caution about the information we share online and advocate for stronger privacy protections at the policy level.
20. Security Orchestration, Automation, and Response (SOAR):
SOAR platforms can help organizations streamline their security operations and respond to threats more efficiently. To maximize the benefits of SOAR, selecting and implementing the right platform for our organization is essential, as is investing in the necessary training for our staff.
Writer:
Enamul Haque
He is a renowned author listed on Amazon, known for his best-selling works on cutting-edge technologies, including cloud computing, artificial intelligence, IoT, data science, and computer science. He is also a thought leader who provides technology advancement consultancy to Fortune 500 companies.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind