Apple released security updates for iOS, macOS, tvOS, visionOS, watchOS, and Safari to fix many vulnerabilities. The IT giant addressed numerous security vulnerabilities, such as authentication and policy bypasses, information disclosure, denial-of-service (DoS) issues, and bugs leading to memory leaks, unexpected application termination, or system shutdown, by releasing iOS 17.6 and …
Read More »TimeLine Layout
August, 2024
-
1 August
A Fortune 50 company paid a record $75 million ransom
Zscaler found out that a company paid the Dark Angels ransomware group a huge ransom of $75 million. However, Zscaler did not reveal the company’s name or any further details about the attack.This is the largest ransomware payment by a company in history. The Dark Angels ransomware group was first …
Read More »
July, 2024
-
31 July
Microsoft Confirms Outage Was Triggered By Cyberattack
Microsoft Azure suffered an outage on July 30 due to a cyberattack known as a distributed denial of service (DDoS) attack. Users complained about not being able to access various Microsoft services yesterday, including Microsoft 365 products like Office, Outlook, and Azure. The incident—which lasted nearly 10 hours—took place less …
Read More » -
30 July
Microsoft Azure and 365 portal hit by global outage
Microsoft is looking into a big problem that is preventing people from accessing certain Microsoft 365 and Azure services. “We’re currently investigating access issues and degraded performance with multiple Microsoft 365 services and features. More information can be found under MO842351 in the admin center,” Redmond said. Many users are …
Read More » -
30 July
SQL database of Bangladesh RTHD’s Training Data compromised
Bangladesh Road Transport and Highways Division (RTHD) experienced a data breach recently. An attacker, who goes by the alias “frog,” successfully accessed the SQL data of RTHD’s Road and Road Training Department. The breach was discovered earlier this week and is being analyzed by the expert team at Bangladesh Cyber …
Read More » -
30 July
CISA Includes Three Recently Exploited Vulnerabilities in Catalog
CISA added three new vulnerabilities to its KEV catalog of actively exploited vulnerabilities. CVE-2024-4879 ServiceNow Improper Input Validation Vulnerability: ServiceNow has addressed an input validation vulnerability that was identified in Vancouver and Washington DC Now Platform releases. This vulnerability could enable an unauthenticated user to remotely execute code within the …
Read More » -
30 July
Bangladesh faces 50,000 cyber attack last 10 days: Minister Palak
State Minister for Posts, Telecommunications and Information Technology Zunayed Ahmed Palak said that 8 websites were attacked over 50,000 times in 10 days. He shared this at a press conference after a meeting on cyber security at the ICT Tower in Agargaon, Dhaka, on Tuesday (July 30). There is a …
Read More » -
30 July
Ransomware Gangs Exploiting VMware ESXi Flaw: Microsoft
Microsoft’s threat intelligence team has reported that ransomware groups are exploiting a critical vulnerability in VMware’s ESXi hypervisors. This allows them to gain full administrative access to systems that are joined to a domain. The flaw labeled CVE-2024-37085 with a severity score of 6.8 has been used by ransomware groups …
Read More » -
29 July
Fiber optic networks ‘sabotaged’ in France: Telecom networks hit
Several fiber optic networks in France were sabotaged shortly after arson attacks disrupted high-speed train services during the Olympics opening ceremony. Cables for telecom operators in six areas of France were intentionally cut earlier today, according to the police. French authorities arrested an activist from an ultra-left-wing movement at an …
Read More » -
29 July
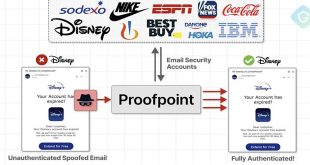
“EchoSpoofing” Exploited Proofpoint flaw to Send Millions of Phishing Emails
A scam campaign linked to an unknown threat actor is using an email routing misconfiguration in Proofpoint’s defenses to send millions of fake emails pretending to be from companies like Best Buy, IBM, Nike, and Walt Disney. Guardio Labs named the campaign EchoSpoofing. It started in January 2024. The threat …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind