GitLab released security updates on Wednesday to fix 17 vulnerabilities, including a critical issue that lets attackers run pipeline jobs as any user. CVE-2024-6678 is a critical vulnerability with a CVSS score of 9.9 out of 10.0 “An issue was discovered in GitLab CE/EE affecting all versions starting from 8.14 prior …
Read More »TimeLine Layout
September, 2024
-
13 September
Fortinet admits data breach after hacker claims to steal 440GB
Fortinet confirmed a data breach after a threat actor claimed to have stolen 440GB of files from its Microsoft SharePoint server. Fortinet told two international media that, “An individual gained unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party cloud-based shared file drive, which …
Read More » -
12 September
Gov.t issues high alert on android devices
Indian Computer Emergency Response Team (CERT-In) issued a high-severity alert for android devices on September 11, 2024 highlighting the vulnerabilities that affect Android versions 12, 12L, 13, and 14. The advisory said, bad attacker could potentially exploit these vulnerabilities to gain access the sensitive information stored in the devices, even …
Read More » -
12 September
TD Bank fined $28 million for sharing customer data
Because of disclosing incorrect and negative data, The Consumer Financial Protection Bureau (CFPB) on Wednesday fined TD Bank, one of North American leading financial institutions $28 million to consumer reporting agencies. According to the agency, The inaccurate data included “systemic errors about credit card delinquencies and bankruptcies,”. Nearly $8 million …
Read More » -
12 September
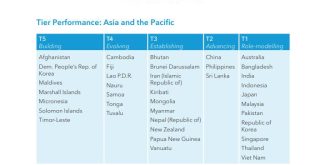
Global-Cybersecurity-Index
Bangladesh secure role-model position by ITUBangladesh secure prestigious role-model position in the latest ITU cyber security index published by ITU. Bangladesh ranks among the top 10 percent of the world’s most cyber-secure countries, according to the latest Global Cyber Security Index 2024 report released by the International Telecommunication Union (ITU) on Thursday. The report places …
Read More » -
12 September
New RansomHub Attack Kill Kaspersky’s TDSSKiller To Disable EDR
Threatdown Managed Detection and Response (MDR) team has discovered the RansomHub ransomware gang using a new attack method wityh two tools: TDSKiller, to disable EDR system, and LaZagne, for stealing credentials. Although both TDSSKiller and LaZagne have been used by attackers for years, this is the first record of RansomHub …
Read More » -
11 September
Not Enough, Say Experts
India set to train 5000 ‘Cyber Commandos’India is to make 5,000 cyber commandos over the next five years to deal with cybercrimes in India, said Home Minister Amit Shah on Tuesday. He urged that cybercrime has no boundary, and hence all stakeholders must come together to deal with its menace. The unit will consist of 5,000 …
Read More » -
11 September
Researcher detect 21 New Ransomwares in August
In August, Cybersecurity researchers identified 21 new ransomware variants that threaten indivisual and business. Cybercriminals are improving their tactics, making it harder to detect and combat these malicious programs. Ransomware encrypts valuable data, making it inaccessible, and then demands high ransoms for decryption keys. This puts personal data at risk …
Read More » -
11 September
Microsoft patch September 2024 fixes 4 zero-days, 79 flaws
Microsoft patched September 2024 Tuesday addressing 79 vulnerabilities, including four actively exploited zero-days which covers critical flaws in Windows Installer, MoTW, Publisher, and Windows Update. Those flaw are mentioned in September 2024 patch Tuesday are rated as critical, most of which were either remote code execution (RCE) or elevation of …
Read More » -
11 September
Zyxel Issues Hotfix for EOL NAS product
Zyxel issued hotfixes for a severe command injection vulnerability traced as CVE-2024-6342, affecting its NAS326 and NAS542 network-attached storage (NAS) devices. The flaw reported by security researchers Nanyu Zhong and Jinwei Dong from VARAS@IIE, poses significant risks for it allows bad actor to execute arbitrary operating system commands. Its concerning …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind