Fazle Hassan Anik hacked girls’ Facebook accounts to steal sensitive pictures, which he used to blackmail them for money. He used the money to pay for his own and his girlfriend’s expenses. In the past two years, Anik blackmailed at least 15 people by hacking over 50 Facebook accounts. He …
Read More »TimeLine Layout
October, 2024
-
27 October
Bangladeshi Social media flooded with unauthorized withdrawals from bank accounts
Bangladeshi Social media posts have raised concerns about unauthorized withdrawals from bank accounts, affecting at least 7 to 8 people who hold dual currency or credit cards. Initial findings suggested two banks are reported to impacted. Bangladesh Cyber Security Intelligence (BCSI) reported unauthorized transactions made via Facebook Ad Manager, often …
Read More » -
25 October
Unprotected UN Database Exposes 228GB of Gender Violence Victims’ Data
Cybersecurity researcher Jeremiah Fowler found a non-password-protected database with 115,000 records linked to the UN Trust Fund to End Violence against Women. This fund aims to prevent violence against women and girls by supporting organizations that address gender-based violence and promote women’s rights. The unprotected database contained sensitive financial reports, …
Read More » -
25 October
Cisco Issues Urgent Fix for ASA and FTD Software Vulnerability
Cisco announced updates on Wednesday to fix a security flaw in its Adaptive Security Appliance (ASA) that is currently being exploited and could cause a denial-of-service (DoS) condition. CVE-2024-20481 (CVSS score: 5.8) is A vulnerability in the Remote Access VPN (RAVPN) service of Cisco Adaptive Security Appliance (ASA) Software and …
Read More » -
23 October
Hackers Earn $500,000 on First Day of Pwn2Own Ireland 2024
White hat hackers at the Pwn2Own Ireland 2024 contest by Trend Micro’s Zero Day Initiative earned $500,000 on the first day by exploiting NAS devices, cameras, printers, and smart speakers. Sina Kheirkhah from Summoning Team earned the top reward of $100,000 by exploiting nine vulnerabilities in an attack from a …
Read More » -
22 October
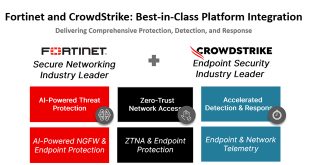
Fortinet + Crowdstrike team on protection from endpoint to firewall
In today’s rapidly changing cybersecurity environment, organizations encounter numerous complex threats targeting endpoints and networks. CrowdStrike and Fortinet have partnered to provide top-notch protection from endpoints to firewalls. This partnership combines the strengths of CrowdStrike in endpoint security and Fortinet in network security, offering customers the flexibility, visibility, and protection …
Read More » -
22 October
Sophos to Acquire Secureworks in $859M
Sophos, based in the UK, is to acquire Secureworks, a Nasdaq-listed company, for $859 million in cash from Dell Technologies. This merger combines two major channel-focused cybersecurity firms. Sophos plans to combine solutions from both companies to create a stronger security portfolio for small, mid-sized, and enterprise customers. Dell owns …
Read More » -
21 October
2nd time hacker breached Internet Archive
The Internet Archive was breached again, this time through their Zendesk email support platform, following warnings that threat actors had stolen exposed GitLab authentication tokens. Bleeping computer reported, Since last night, the authority received numerous messages from people who received replies to their old Internet Archive removal requests, warning that …
Read More » -
20 October
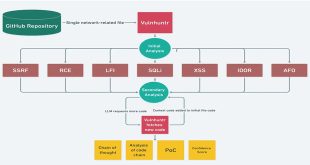
Vulnhuntr: A Tool for Finding Exploitable Vulnerabilities with LLMs
In today’s changing cybersecurity environment, it’s essential to find vulnerabilities in code. Vulnhuntr, an open-source tool on GitHub, uses Large Language Models (LLMs) and static code analysis to detect remotely exploitable vulnerabilities in Python projects. Its user-friendly design combines intelligent automation with thorough code analysis, making it a valuable resource …
Read More » -
18 October
Critical Vulnerabilities in Bitdefender Total Security Expose Users to MITM
Bitdefender said a vulnerability has been identified in Bitdefender Total Security HTTPS scanning functionality where the software fails to properly validate website certificates. Specifically, if a site certificate lacks the “Server Authentication” specification in the Extended Key Usage extension, the product does not verify the certificate’s compliance with the site, …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind