A whistleblower from OpenAI, Suchir Balaji, an Indian-American ex-researcher at OpenAI who criticized the company’s practices, was found dead in his San Francisco apartment on November 26. Anandabazar said, Primarily the police suspect it to be a case of suicide. Balaji, who left OpenAI in August after four years, was …
Read More »TimeLine Layout
December, 2024
-
14 December
Canadian company exposed unprotected almost 5 million records
Cybersecurity expert, Jeremiah Fowler discovered an unsecured database containing almost 5 million records reportedly relating to Care1 — a Canadian company offering AI software solutions. He reported to VPN mentor that the publicly exposed database was unprotected, passwordless, and not encrypted, totaling 2.2 TB. It included records in PDF format …
Read More » -
13 December
Daily Security Update Dated: 13.12.2024
Every day a lot of cyberattack happen around the world including ransomware, Malware attack, data breaches, website defacement and so on. Its our daily security digest to cover the latest happenings in the world. Spend a bit time to read out todays update: Cybercriminals are paying pentesters to vet their …
Read More » -
13 December
GitLab flaw allow Bitcoin ATM giant “Byte Federal” hacked
TechCrunch reports that Byte Federal, a major Bitcoin ATM operator in the U.S., has experienced a data breach affecting the personal information of thousands of customers. A Florida-based company recently reported to the Maine attorney general that hackers tried to access data from about 58,000 customers. The breached information includes …
Read More » -
12 December
CVE-2024-11274
GitLab Patch Release for CE and EEGitLab has released a critical security update for several versions of its platform, including versions 17.6.2, 17.5.4, and 17.4.6 for both Community and Enterprise Editions. This update fixes vulnerabilities that could result in account takeovers, denial of service attacks, and data leaks. CVE-2024-11274 (CVSS 8.7) is a critical vulnerability that …
Read More » -
12 December
Researcher claim to bypass Microsoft Azure MFA flaw within hour
Oasis Security discovered a flaw in Microsoft’s Multi-Factor Authentication (MFA) system, allowing attackers to bypass it and access user accounts, including Outlook, OneDrive, Teams, and Azure. With over 400 million Office 365 users, the impact of this vulnerability could be significant. Research team claim, “The bypass was simple: it took …
Read More » -
12 December
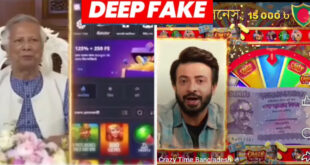
Meta fails to detect
9 Deepfake videos identified of Dr. Md. Yunus and Shakib KhanDr. Md. Yunus, the chief advisor to the interim government of Bangladesh, is the victim of propaganda using artificial intelligence. A Deepfakes video of him has been seen on social media for the past few days where he is heard saying on the gambling site, “I have decided to create …
Read More » -
12 December
Facebook, Instagram, and Threads are reportedly down
Facebook, Instagram and threads are experiencing technical issues, causing temporary disruptions worldwide. Many users are having trouble messaging, and Meta has not yet commented on the cause of the outage. Around 11:30 pm on Wednesday, many users experienced login issues with the web version of WhatsApp, receiving a ‘service not …
Read More » -
11 December
U.S. Charges Chinese man linked to global Firewall hack
A federal court in Hammond, Indiana, has unsealed an indictment against Guan Tianfeng, a Chinese citizen, for allegedly hacking firewall devices globally in 2020. Guan and his co-conspirators, employed by Sichuan Silence Information Technology Co. Ltd., targeted a previously unknown vulnerability (an “0-day” vulnerability) in firewalls produced by U.K.-based Sophos …
Read More » -
11 December
Hackers Exploit AWS Misconfigurations: allegedly 2TB data lost
Thousands of AWS customers had terabytes of sensitive data, including personal details, AWS credentials, and proprietary code, compromised in a cyber attack linked to the ShinyHunters hacking group. They gained access to sensitive information through poorly set up systems, resulting in over 2 TB of compromised data. Cybersecurity researchers Noam …
Read More »
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind