A new Android malware called SikkahBot is targeting students in Bangladesh by pretending to be official apps from the Bangladesh Education Board. Cyble Research and Intelligence Labs (CRIL) found that this malware has been active since July 2024.
According to CRIL, the SikkahBot malware is distributed through shortened URLs, including links like bit[.]ly/Sikkahbord, apped[.]short[.]gy, and downloadapp[.]website/tyup[.]apk. These URLs are likely spread through smishing attacks, tricking victims into downloading malicious APK files under the pretense of scholarship applications from government bodies.
The download URLs associated with this campaign are listed below.
hxxps://bit[.]ly/Sikkahbord
hxxps://bit[.]ly/Education-2025
hxxps://bit[.]ly/Educ-govt
hxxps://bit[.]ly/app-upobitti
hxxps://bit[.]ly/D43SJ
hxxp://sbs[.]short[.]gy/
hxxps://apped[.]short[.]gy/
hxxps://downloadapp[.]website/tyup[.]apk
hxxps://appsloads[.]top/govt[.]apk
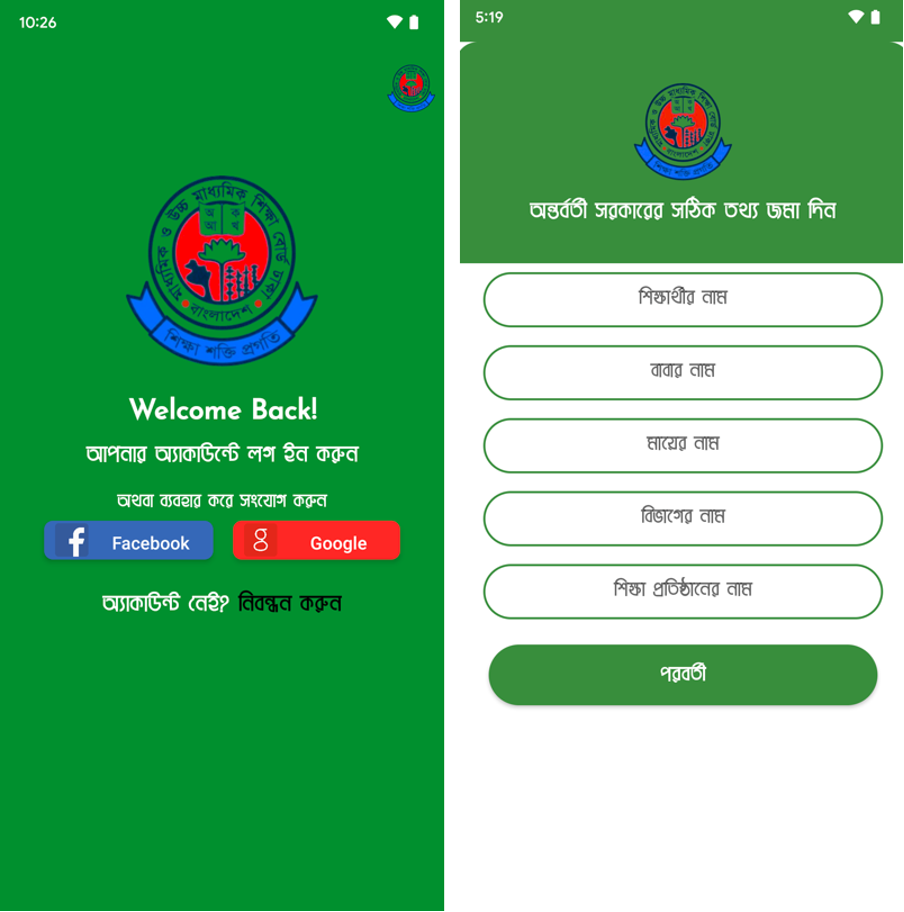
Fake apps prompt users to log in with Google or Facebook and ask for personal information like name and department. They also request financial details such as wallet numbers and PINs. After the victim submits the info, they receive a fake message saying a representative will reach out, giving the malware time to operate in the background.
SikkahBot Malware: Permissions Abuse and Automated Banking Fraud
SikkahBot stands out due to its aggressive use of Android permissions. When installed, it pressures users to grant risky access like Accessibility Service, SMS access, call management, and the ability to draw over other apps. This lets it closely monitor and control user activity on the device.
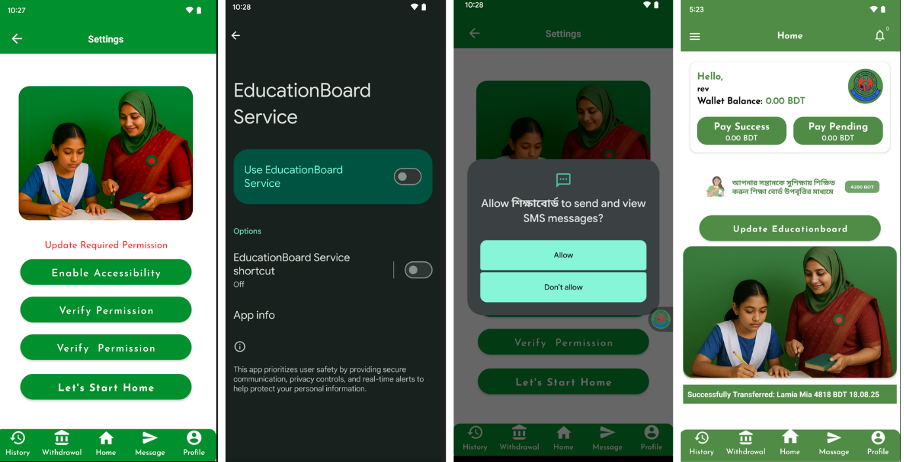
After granting permissions, the malware displays a fake homepage with edited images of students appearing to receive scholarships. This is part of its tactic to appear legitimate.
Behind the scenes, SikkahBot registers a broadcast receiver to intercept all incoming SMS messages. It specifically targets keywords related to mobile banking services widely used in Bangladesh, such as “bKash,” “Nagad,” and “MYGP,” as well as associated service numbers like “16216” and “26969.” Captured messages are then sent to an attacker-controlled Firebase server at update-app-sujon-default-rtdb[.]firebaseio.com.
Accessibility Exploits and Offline USSD Transactions:
The malware exploits Accessibility Service, posing a serious threat. When it identifies user activity in banking apps like bKash, Nagad, or Dutch-Bangla Bank, it retrieves credentials from its server and autofills login details without user input.
If the user isn’t actively using these apps, SikkahBot initiates USSD-based banking transactions. It receives USSD codes and SIM slot information from the server, executes the calls, and automatically interacts with response prompts by clicking on UI elements labeled “SEND” or “OK.” This method allows transactions without requiring internet access, increasing the malware’s reach and reliability in low-connectivity environments.
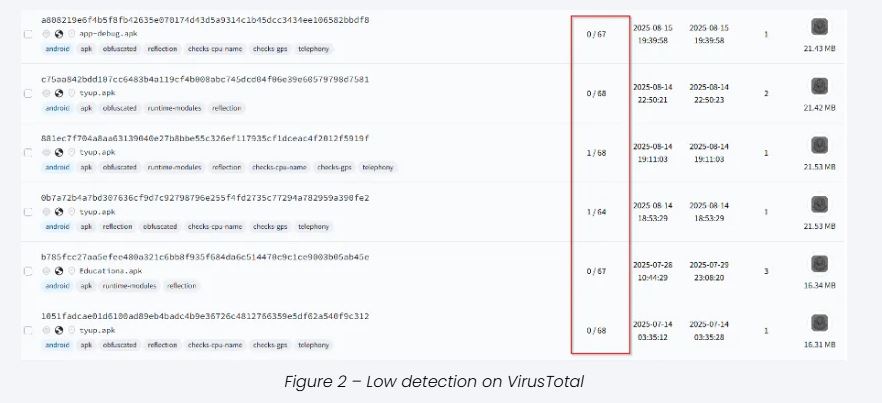
Evasion and Evolution:
SikkahBot malware variants have low detection rates on VirusTotal due to their obfuscation techniques and ongoing improvements by attackers. CRIL reports over 10 distinct samples, with newer versions featuring more automation and advanced command execution methods.
“The combination of phishing, automated banking activity, and offline USSD exploitation makes it a highly effective tool for financial fraud against unsuspecting students,” CRIL stated in its technical analysis.
Recommendations:
Cyble listed some essential cybersecurity best practices that create the first line of control against attackers.
Install Apps Only from Trusted Sources:
Download apps exclusively from official platforms like the Google Play Store. Avoid third-party app stores or links received via
SMS, social media, or email.
Be Cautious with Permissions:
Never grant accessibility services or overlay permissions unless you’re certain of an app’s legitimacy.
Watch for Phishing Pages:
Always verify the URL and avoid suspicious links and websites that ask for sensitive information.Enable Multi-Factor Authentication (MFA): Use MFA for banking and financial apps to add an extra layer of protection, even if credentials are compromised.
Use Mobile Security Solutions:Install a mobile security application that includes real-time scanning.
Keep Your Device Updated: Ensure your Android OS and apps are updated regularly. Security patches often address vulnerabilities exploited by malware.
South Asian APT to Compromise Phones of Military-linked Individuals In Bangladesh
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind