According to ESET, Russia linked Ramcom exploit the two zero days of Mozilla FireFox and Microsoft Window addressed CVE 2024-9680, and 2024-49039.
“In a successful attack, if a victim browses a web page containing the exploit, an adversary can run arbitrary code – without any user interaction required (zero click) – which in this case led to the installation of RomCom’s backdoor on the victim’s computer,” ESET said.
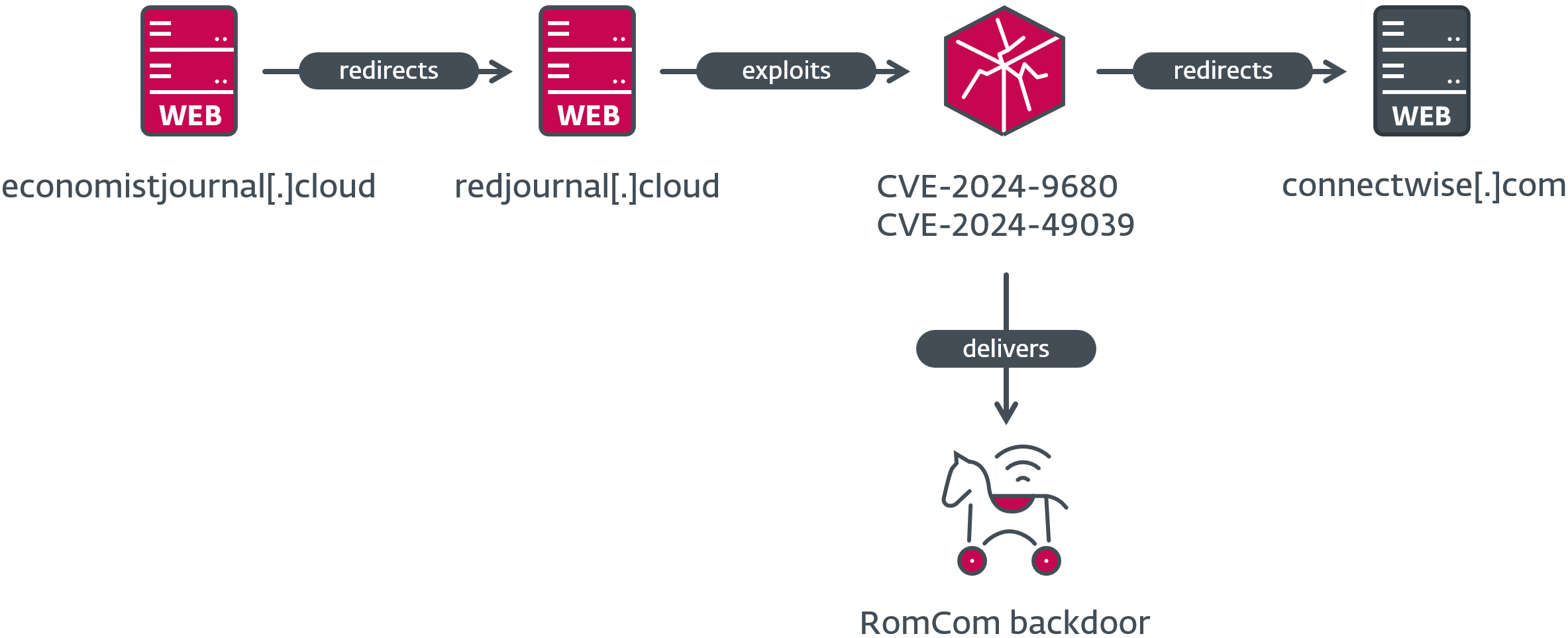
CVE-2024-9680 (Patched by Mozilla in October 2024) is a critical vulnerability (CVSS score 9.8) affecting Firefox, Thunderbird, and the Tor Browser, allowing code execution in the browser’s restricted environment. When combined with another vulnerability in Windows (CVE-2024-49039, CVSS score 8.8, Patched by Microsoft in November 2024), it enables arbitrary code execution as the logged-in user. If a victim visits an exploit-laden web page, an attacker can execute code without user interaction, ultimately installing the RomCom backdoor on the victim’s system.
CVE-2024-9680 let attackers execute code within the browser, while CVE-2024-49039 allowed code to run outside Firefox’s sandbox, both without any interaction from the victims.
ESET researcher Damien Schaeffer discovered that the compromise chain involves a fake website that redirects victims to a server with a zero-click exploit. If this exploit is triggered, shellcode downloads and executes the RomCom backdoor.
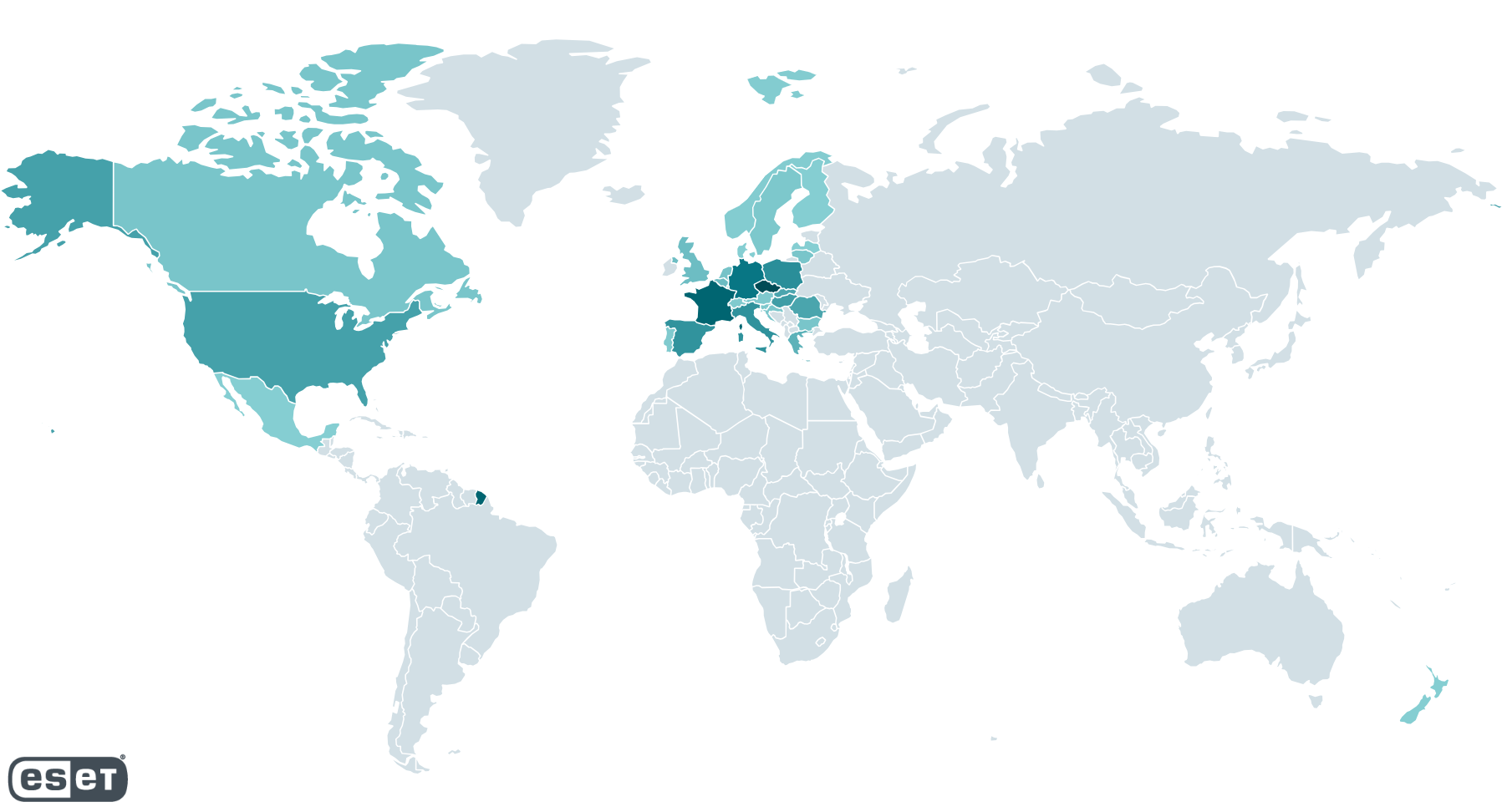
ESET’s telemetry data reveals that most victims of the exploit-hosting site were in Europe and North America.
The independent discovery of CVE-2024-49039 by Google’s Threat Analysis Group (TAG) indicates that multiple threat actors could be exploiting it as a zero-day vulnerability.
RomCom has been caught exploiting a zero-day vulnerability for the second time, previously using CVE-2023-36884 in Microsoft Word in June 2023.
RomCom (also known as Storm-0978, Tropical Scorpius, or UNC2596) is a Russia-aligned threat group involved in opportunistic attacks on various industries and targeted espionage.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














