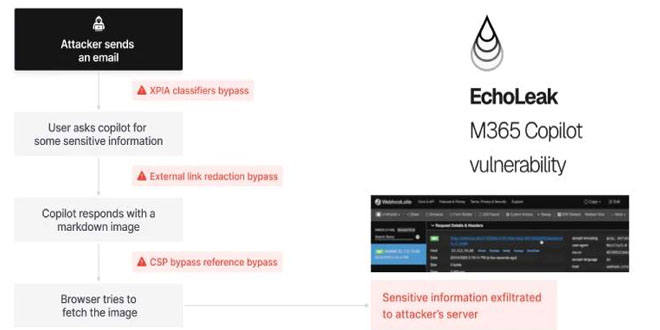
Security vulnerabilities in Apple’s AirPlay Protocol and SDK put both third-party and Apple devices at risk of various attacks, including remote code execution.
Oligo Security researchers found flaws that can be exploited in zero-click and one-click remote code execution (RCE) attacks, man-in-the-middle (MITM) attacks, denial of service (DoS) attacks, and can bypass access control lists (ACLs) and user interactions. These vulnerabilities allow access to sensitive information and arbitrary local files.
Oligo reported 23 security vulnerabilities to Apple, which released updates on March 31 to fix these issues, collectively called “AirBorne.” The updates apply to iPhones and iPads (iOS 18.4 and iPadOS 18.4), Macs (macOS Ventura 13.7.5, macOS Sonoma 14.7.5, and macOS Sequoia 15.4), and Apple Vision Pro (visionOS 2.4).
The company updated the AirPlay audio SDK, AirPlay video SDK, and CarPlay Communication Plug-in.
AirBorne vulnerabilities can be exploited by attackers on the same wireless network, allowing them to take control of vulnerable devices and use them to compromise other AirPlay-enabled devices on the network.
Oligo’s security researchers for demonstrated that attackers can exploit two security flaws (CVE-2025-24252 and CVE-2025-24132) to create wormable zero-click RCE exploits.
The CVE-2025-24206 flaw allows attackers to bypass the “Accept” click requirement on AirPlay requests, enabling them to launch zero-click attacks when combined with other vulnerabilities.
“This means that an attacker can take over certain AirPlay-enabled devices and do things like deploy malware that spreads to devices on any local network the infected device connects to. This could lead to the delivery of other sophisticated attacks related to espionage, ransomware, supply-chain attacks, and more,” Oligo warned.
“Because AirPlay is a fundamental piece of software for Apple devices (Mac, iPhone, iPad, AppleTV, etc.) as well as third-party devices that leverage the AirPlay SDK, this class of vulnerabilities could have far-reaching impacts.”
The cybersecurity company advises organizations to immediately update any corporate Apple devices and AirPlay-enabled devices to the latest software release and ask employees to also update all their personal AirPlay devices.
Users can minimize their attack surface by updating all Apple devices to the latest version, disabling the AirPlay receiver if it’s not in use, restricting AirPlay access to trusted devices with firewall rules, and only allowing AirPlay for the current user.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind