Researchers found a big phishing campaign that uses QR codes to trick people. QR code fraud or “quishing” is a type of phishing where hackers pretend to be a trustworthy source to trick people into giving sensitive information or downloading malware.
This trend is concerning and should not be ignored. It puts both individuals and organizations at high risk.
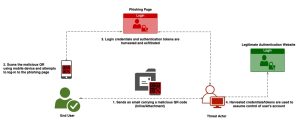
Interpol seized 16 shops that were a well-known phishing platform, a big win. But “phishing-as-a-service” platforms make it even easier to launch attacks.
The popularity of QR codes creates a perfect storm for phishing attacks. Trellix’s research provides important insights about the seriousness of the threat. More than 60,000 quishing samples were found in just one quarter. They used different tactics like postal phishing, spear phishing, and malware delivery to target users.
To understand how quishing works, let’s delve into the “Quishing Kill Chain”:
Attackers distribute malicious QR codes: These codes can be found anywhere.
Unsuspecting victims scan the codes: This action leads to harmful websites.
Attackers achieve their malicious goals: This could involve unauthorized access or causing additional harm.
The resurgence of QR codes has paved the way for quishing to flourish. Attackers abuse our trust in codes and our tendency to act quickly when in a hurry. This makes people and organizations vulnerable to advanced phishing tactics.
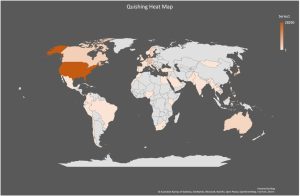
Trellix’s research reveals insightful details about recent quishing campaigns:
Postal quishing: Emails posing as FedEx and DHL exploit delivery concerns, redirecting recipients to counterfeit login pages.
Spear quishing: tricking employees with fake emails
File-share quishing: shady links disguised as legitimate documents.
Crypto wallet quishing: Stealing crypto wallet phrases and private keys from impersonated Coinbase and Binance.
To prevent falling victim to quishing, here are some essential tips:
Only scan QR codes from trusted sources: Verify the legitimacy of any code before scanning.
Check if the QR code is from a trustworthy source like an email, website, or location.
Do not provide personal information after scanning a QR code.
Invest in email security and anti-malware software to protect your devices.
Stay informed and keep up-to-date about the latest phishing tactics. Make sure to educate others about the tactic known as “quishing”.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind