Palo Alto Networks has revealed a high severity vulnerability in PAN-OS software that may lead to a denial-of-service (DoS) issue on affected devices.
The vulnerability CVE-2024-3393 (CVSS score: 8.7) affects PAN-OS versions 10.X and 11.X, and Prisma Access with PAN-OS versions 10.2.8 or later and before 11.2.3. It has been fixed in PAN-OS versions 10.1.14-h8, 10.2.10-h12, 11.1.5, 11.2.3, and all newer versions.
By infosecbulletin
/ Saturday , September 13 2025
F5 plans to acquire CalypsoAI, which offers adaptive AI security solutions. CalypsoAI's technology will be added to F5's Application Delivery...
Read More
By infosecbulletin
/ Saturday , September 13 2025
The Villager framework, an AI-powered penetration testing tool, integrates Kali Linux tools with DeepSeek AI to automate cyber attack processes....
Read More
By infosecbulletin
/ Saturday , September 13 2025
Samsung released its monthly Android security updates, addressing a vulnerability exploited in zero-day attacks. CVE-2025-21043 (CVSS score: 8.8) is a...
Read More
By infosecbulletin
/ Saturday , September 13 2025
Albania has appointed the first AI-generated government minister to help eliminate corruption. Diella, the digital assistant meaning Sun, has been...
Read More
By infosecbulletin
/ Thursday , September 11 2025
On September 1, 2025, Qrator Lab identified and managed a major attack from the largest L7 DDoS botnet seen so...
Read More
By infosecbulletin
/ Thursday , September 11 2025
A new vulnerability, CVE-2025-4235, in Palo Alto Networks’ User-ID Credential Agent for Windows, could reveal a service account's password in...
Read More
By infosecbulletin
/ Thursday , September 11 2025
CyberVolk ransomware, which appeared in May 2024, has increased attacks on government agencies and critical infrastructures in Japan, France, and...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Microsoft has issued a new warning about a critical security vulnerability in Active Directory Domain Services, known as CVE-2025-21293. An...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The...
Read More
By infosecbulletin
/ Wednesday , September 10 2025
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and...
Read More
“A denial-of-service vulnerability in the DNS Security feature of Palo Alto Networks PAN-OS software allows an unauthenticated attacker to send a malicious packet through the data plane of the firewall that reboots the firewall,” the company said in a Friday advisory.
“Repeated attempts to trigger this condition will cause the firewall to enter maintenance mode.”
Palo Alto Networks said it discovered the flaw in production use, and that it’s aware of customers “experiencing this denial-of-service (DoS) when their firewall blocks malicious DNS packets that trigger this issue.”
The activity’s scope is currently unclear. Hacker News has contacted Palo Alto Networks for comment and will update the story if they respond.
Firewalls with DNS Security logging enabled are affected by CVE-2024-3393. The flaw’s severity is reduced to a CVSS score of 7.1 when access is limited to authenticated users through Prisma Access.
The fixes have also been extended to other commonly deployed maintenance releases –
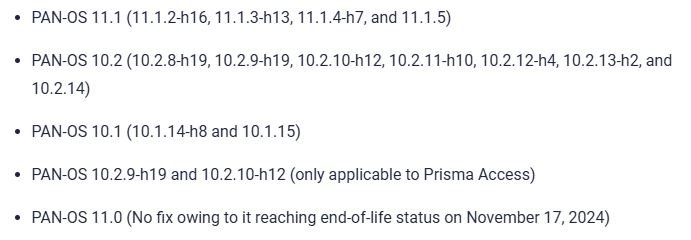
As workarounds and mitigations for unmanaged firewalls or those managed by Panorama, customers have the option of setting Log Severity to “none” for all configured DNS Security categories for each Anti-Spyware profile by navigating to Objects > Security Profiles > Anti-spyware > (select a profile) > DNS Policies > DNS Security.
Users can disable DNS Security logging on firewalls managed by Strata Cloud Manager (SCM) either individually or for all devices by opening a support case. For Prisma Access tenants, it’s recommended to open a support case to disable logging until an upgrade is performed.

 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














