OWASP released the LLM AI Cybersecurity & Governance Checklist. The 32-page document helps organizations create a strategy for using large language models and reducing associated risks.
Sandy Dunn, CISO at Quark IQ, started working on the checklist in August 2023 as a supporting resource to OWASP’s Top 10 Security Issues for LLM Applications, published in the summer of 2023.
“I created the first version to help CISOs and cybersecurity professionals who were confused about what they needed to consider and where to begin with AI,” she said.
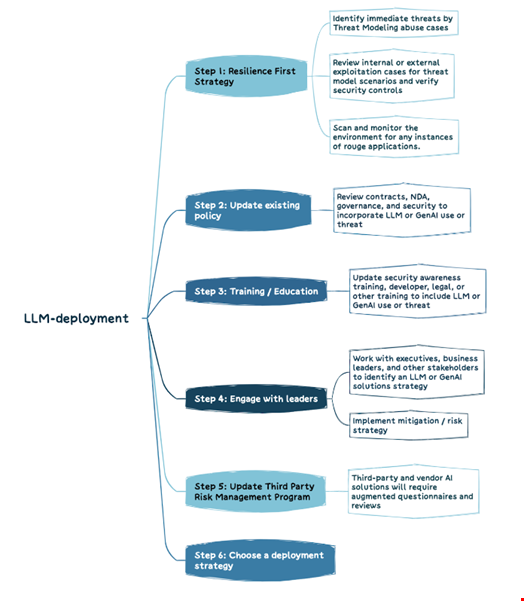
Steps to Take Before Implementing an LLM Strategy:
Review your cyber resilience and security training strategies and engage with leaders about AI implementation into your workflow as steps before deploying an LLM strategy.
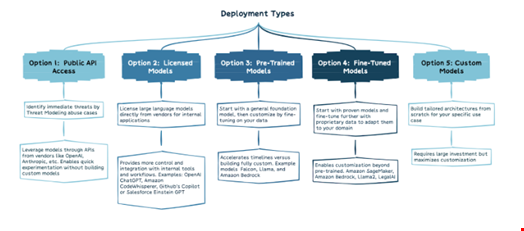
It gives an overview of five ways organizations can use LLMs based on their needs.
The document states that it is important to consider factors such as the sensitivity of the use case, the required capabilities, and the available resources in order to determine the right balance between convenience and control when using public consumer applications or training proprietary models on private data.
Dunn said that even though the list isn’t complete, understanding these five model types is a practical starting point for evaluating options.
The document lists 13 things to consider when implementing an LLM use case to avoid unnecessary risk.
Dunn commented: “The four things I really wanted people to take from the checklist were the following:
Generative AI is a vastly different technology than we’ve tried to protect organizations from before and it will require a completely different mindset to protect an organization;
AI brings asymmetrical warfare: The adversary has an advantage because of the complexity and breadth of the attack surface. The first thing to address is how fast attackers will be able to use these tools to accelerate their attacks, which we are already seeing;
Approach AI implementation holistically;
Use existing legislation to inform your strategy: Even though very few AI laws are currently enforceable, many existing laws like the EU’s General Data Protection Regulation (GDPR) and privacy and security state laws impact your AI business requirements.”
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














