With over 211,000 followers, the official Microsoft India account on Twitter was hijacked by cryptocurrency scammers impersonating Roaring Kitty. This account has a gold check mark as an officially verified organization.

The threat actors take advantage of Gill’s recent comeback to lure potential victims and infect them with cryptocurrency wallet drainer malware.
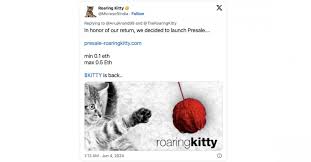
According to Bleeping Computer, they are now using Microsoft India’s hijacked account to reply to tweets, luring the company’s followers and other people on X to a malicious website (presaIe-roaringkitty[.]com) that would allegedly allow them to buy GameStop (GME) crypto as part of a so-called presale.
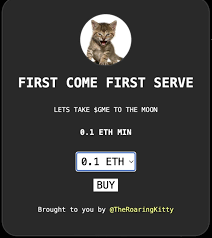
According to thecyberexpress, although these posts have been removed, the hackers continue to repost their stuff from their account on the Microsoft India X account, which has not yet been restored.
Previous X account hacked history;
Hijacking of Microsoft India X account is not a new incident, in fact it is part of a worrying trend where verified X accounts are targeted by scammers. Previously, the U.S. Securities and Exchange Commission (SEC) confirmed that its verified X account was hacked due to a SIM-swapping attack on the phone number linked to the account.
Similarly, the official X accounts of tech giant Netgear and Hyundai MEA (Middle East & Africa) were also hacked, spreading malware to steal from cryptocurrency wallets. These accounts had over 160,000 followers combined.
Other high-profile breaches include accounts of well-known entities and individuals like the cybersecurity firm Mandiant, Ethereum co-founder Vitalik Buterin, and Donald Trump Jr. Most of these hacks are linked to Bitcoin scams, highlighting a troubling pattern in the digital world. These compromised accounts endanger their followers and pose a significant security risk to X’s 528 million users
Source: Bleeping Computer. Thecyberexpress.com, mspoweruser.com
(Media Disclaimer: This report is based on research conducted internally and externally using different ways. The information provided is for reference only, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














