ELUSIVE COMET is a threat actor conducting a sophisticated attack campaign that uses Zoom’s remote control feature to access victims’ computers without permission.
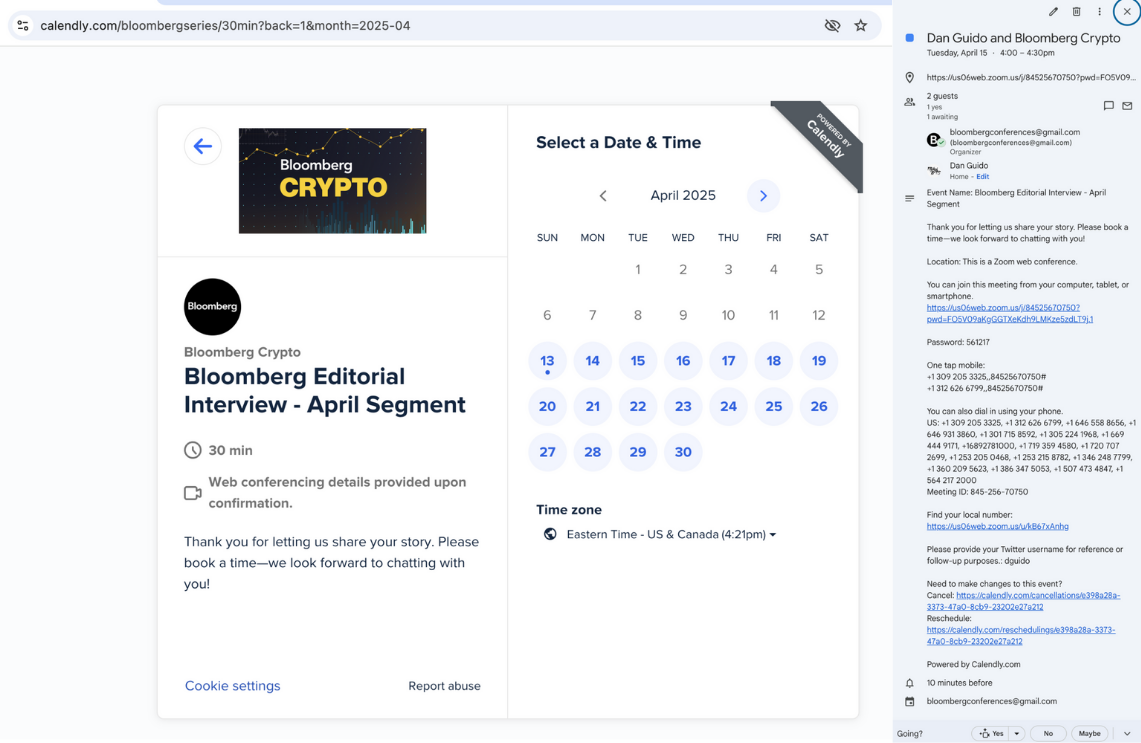
The ELUSIVE COMET operation begins with attackers masquerading as legitimate media organizations, specifically “Bloomberg Crypto,” to invite high-profile targets for interviews.
Invitations are sent through social media, like Twitter (X), using fake accounts that pretend to be real industry professionals. The attackers avoid regular email and direct victims to dubious Calendly booking pages that initially seem professional.
When the target joins the Zoom call, the attack exploits a major vulnerability in Zoom’s user experience design.
Attackers exploit Zoom’s remote control feature during screen sharing by changing their display name to “Zoom,” making their access request look like a system notification.
The permission dialog says, “$PARTICIPANT is requesting remote control of your screen,” which is confusing and potentially risky.
“This attack exploits the permission dialog’s similarity to other harmless Zoom notifications,” notes the Trail of Bits report.
“Users habituated to clicking ‘Approve’ on Zoom prompts may grant complete control of their computer without realizing the implications.”
Attackers can take full control of the victim’s computer, enabling them to steal personal information, install harmful software, or conduct unauthorized transactions.
This approach resembles the methods used in February’s $1.5 billion Bybit hack, suggesting a move towards operational security failures instead of technical flaws.
Organizations handling sensitive information should consider uninstalling Zoom using the uninstall_zoom.bash script and switching to more secure browser-based alternatives.
“As we’ve entered the era of operational security failures, organizations must evolve their defensive posture to address these human-centric attack vectors,” reads the report.
Cryptocurrency organizations must adopt a multi-layered defense that includes technical controls, user training, and operational security awareness to prevent advanced attacks.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind