The hacking group “Belsen Group” has posted over 15,000 unique FortiGate firewall configurations online. The data dump, reportedly obtained by exploiting a zero-day vulnerability in Fortinet’s systems in October 2022, contains sensitive information including usernames, passwords (some in plain text), device management certificates, and complete firewall rules.
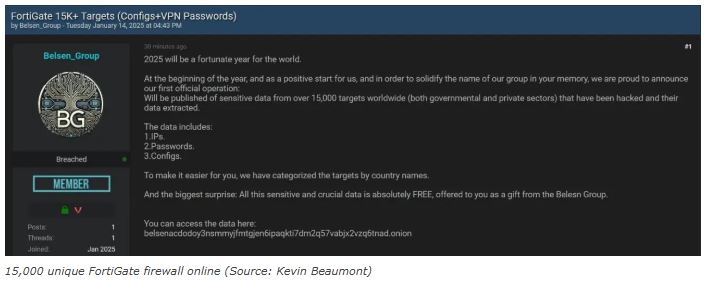
“At the beginning of the year, and as a positive start for us, and in order to solidify the name of our group in your memory, we are proud to announce our first official operation: Will be published of sensitive data from over 15,000 targets worldwide (both governmental and private sectors) that have been hacked and their data extracted,” reads a hacking forum post.
The FortiGate leak is a 1.6 GB archive with subfolders for each FortiGate IP address within those countries. Cybersecurity researcher Kevin Beaumont confirmed the leak’s legitimacy by cross-referencing serial numbers from the data with devices listed on Shodan, a search engine for internet-connected devices.
According to Heise security, the published data doesn’t appear to be linked to recently published vulnerabilities in the FortiOS appliance operating system.
The analysis of the configuration files revealed that all the FortiOS versions in the data set were older than version 7.2.2, released in October 2022.
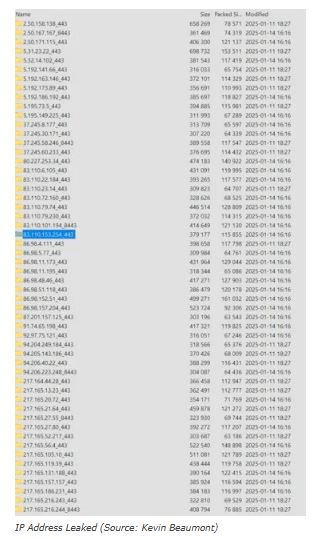
“The build date coded in the last number block also points to the same date range: None of the firewall firmwares examined had been compiled after September 14, 2022.” reported Heise Security.
Bleeping Computer reported, In 2022, Fortinet warned that threat actors were exploiting a zero-day tracked as CVE-2022–40684 to download config files from targeted FortiGate devices and then add a malicious super_admin account called ‘fortigate-tech-support’.
Exploitation of CVE-2022-40684:
The breach traces back to CVE-2022-40684, a critical authentication bypass vulnerability in Fortinet’s FortiOS, FortiProxy, and FortiSwitchManager products.
Attackers could bypass admin authentication through crafted HTTP or HTTPS requests due to this flaw. It was first reported by Fortinet in October 2022 and had a CVSS score of 9.8, indicating it was extremely critical.
Source: BleepingComputer, cyberdaily, cybersecuritynews, securityaffairs
(Media Disclaimer: This report is based on research conducted internally and externally using different ways. The information provided is for reference only, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














