A new proof-of-concept tool named EDR-Freeze has been developed, capable of placing Endpoint Detection and Response (EDR) and antivirus solutions into a suspended “coma” state.
Zero Salarium’s technique uses a built-in Windows feature, providing a stealthy option compared to the rising trend of Bring Your Own Vulnerable Driver (BYOVD) attacks that hackers employ to turn off security software.
This method eliminates the need for third-party drivers, lowering the risk of system issues and detection. It operates entirely in user-mode, effectively and discreetly disabling security monitoring.
The MiniDumpWriteDump Exploit:
The EDR-Freeze technique mainly involves manipulating the MiniDumpWriteDump function, which is from the Windows DbgHelp library and is used to create a minidump—a memory snapshot of a process for debugging.
To ensure a consistent and uncorrupted snapshot, the function suspends all threads within the target process while the dump is created.
Ordinarily, this suspension is brief. However, the developer of EDR-Freeze devised a method to prolong this suspended state indefinitely.
The main challenges were extending the quick execution time of the MiniDumpWriteDump function and getting past the Protected Process Light (PPL) security feature that protects EDR and antivirus processes from interference.
To overcome PPL protection, the technique utilizes WerFaultSecure.exe, a component of the Windows Error Reporting (WER) service. WerFaultSecure.exe can run with WinTCB level protection, one of the highest privilege levels, allowing it to interact with protected processes.
WerFaultSecure.exe can be set to run the MiniDumpWriteDump function on any process, even those of protected EDR and antivirus software, by using the right parameters.
A race-condition attack can turn a brief pause into a lasting freeze, occurring in a quick, exact sequence:
- WerFaultSecure.exe is launched with parameters directing it to create a memory dump of the target EDR or antivirus process.
2. The EDR-Freeze tool continuously monitors the target process.
3. The moment the target process enters a suspended state (as MiniDumpWriteDump begins its work), the EDR-Freeze tool immediately suspends the WerFaultSecure.exe process itself.
Because WerFaultSecure.exe is now suspended, it can never complete the memory dump operation and, crucially, can never resume the threads of the target EDR process.
Zero Salarium stated that the security software remains permanently suspended and ineffective until the WerFaultSecure.exe process is ended.
EDR-Freeze Tool Killing Process:
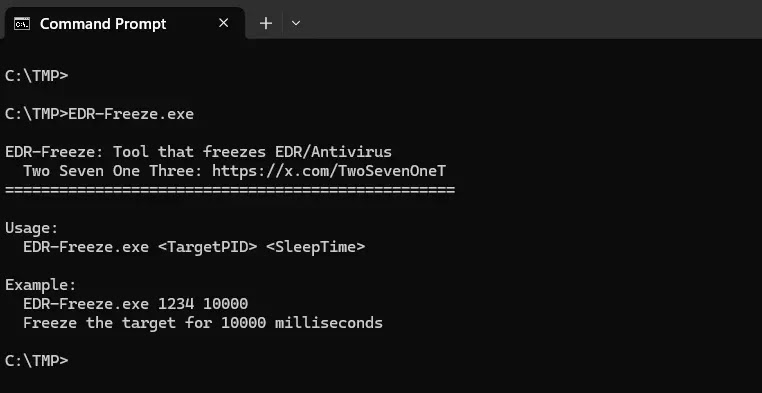
The developer released the EDR-Freeze tool to showcase this technique. It requires two parameters: the Process ID (PID) of the target and the suspension duration in milliseconds.
An attacker can disable security tools, carry out harmful actions, and then restore security software to normal as if nothing occurred.
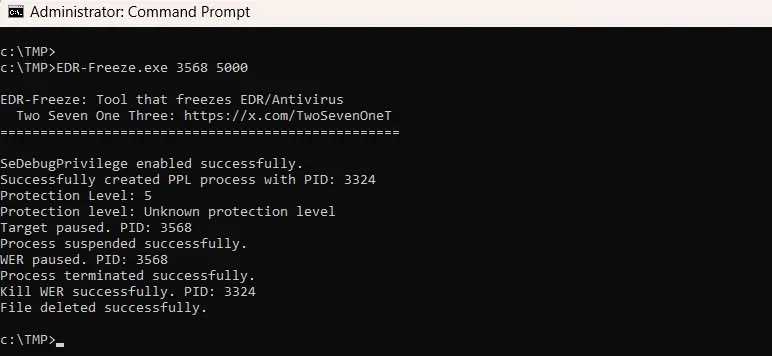
A test on Windows 11 24H2 successfully suspended the MsMpEng.exe process of Windows Defender.
For defenders, detecting this technique involves monitoring for unusual executions of WerFaultSecure.exe.
If the program is observed targeting the PIDs of sensitive processes like lsass.exe or EDR agents, it should be treated as a high-priority security alert requiring immediate investigation.
Source: zerosalarium, cybersecurity news
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind