A security breach has been reported, with a threat actor claiming to be selling a database with 49 million customer records from Dell. The data includes information on systems bought from Dell between 2017 and 2024.
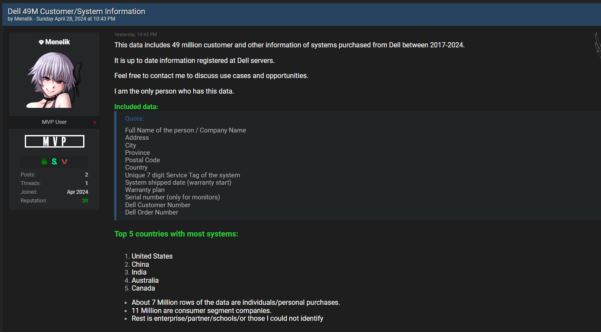
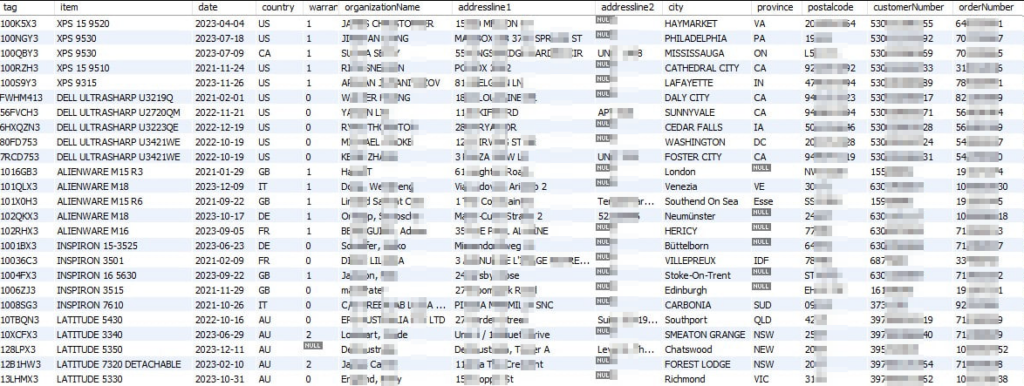
According to Daily dark web, recent data obtained from Dell servers includes sensitive personal and company information. The data is said to be in the possession of a threat actor, emphasizing the seriousness of the breach. It consists of millions of records, with a large portion related to individual purchases and consumer segment companies. The remaining data is linked to enterprise, partner, schools, or unidentified entities. The threat actor also highlights the top five countries with the most systems represented in the database. This situation raises major concerns about the security and privacy of Dell customers’ information, calling for immediate action to reduce risks and prevent unauthorized access.
Bleeping Computer reported that “Dell does not “believe there is significant risk to our customers given the type of information involved,” yet the stolen information could potentially be used in targeted attacks against Dell customers.
As the stolen information does not include email addresses, threat actors could target specific people with physical mailings with phishing links or that contain media (DVDs/thumb drives) to install malware on targets’ devices.
While this may sound far-fetched, threat actors have conducted similar attacks in the past, physically mailing tampered Ledger hardware wallets that stole cryptocurrency or sending gifts with USB drives that installed malware.
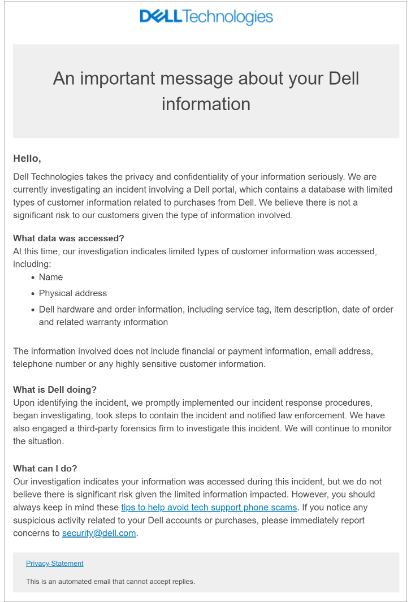
What Dell is Doing?
Dell has notified law enforcement and engaged a forensic firm to investigate the incident. This type of data exposure not only leaves individuals vulnerable to physical harm but also opens the door for threat actors to exploit the information in long-term social engineering attacks.
Customers are at considerable risk due to the sale of data containing full names and physical addresses. This type of data exposure not only leaves individuals vulnerable to physical harm but also opens the door for threat actors to exploit the information in long-term social engineering attacks.
Customers by Country:
The hacker disclosed the countries with the highest number of affected Dell customers incuding India, China, Canada, Australia, United States.
(Media Disclaimer: This report is based on research conducted internally and externally using different ways. The information provided is for reference only, and users are responsible for relying on it. Infosecbulletin is not liable for the accuracy or consequences of using this information by any means)
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














