Researchers have identified a new Crypto24 ransomware campaign, which they describe as a “dangerous evolution” in cybersecurity threats.
According to Trend Micro researchers, recent attacks by Crypto24 actors display a combination of advanced evasion techniques and custom tools that can disable EDR solutions — including Trend Micro’s own Vision One platform. Crypto24 was first spotted in 2024 but hadn’t made much of impact until recently, when it became the latest ransomware gang to bypass EDR platforms and security solutions.
Trend Micro’s report, released on Thursday, highlights Crypto24’s exceptional skills that distinguish it from other ransomware groups. Researchers observed that Crypto24 effectively uses various tools, such as legitimate software like PSExec and AnyDesk for remote access, and Google Drive for data exfiltration.
“More importantly, Crypto24’s successful deployment of a customized RealBlindingEDR (an open source tool for disabling security solutions) variant that neutralized our security controls shows their capability to maneuver around modern defenses,” the report said. “The threat actor’s customized version employs advanced evasion, likely via unknown vulnerable drivers, showcasing deep technical expertise and ongoing tool refinement.”
Trend Micro researchers said Crypto24 actors’ demonstrated “uncommon” strategic planning and patience in these attacks, which have been primarily focused on large enterprises in Asia, Europe, and the US in the financial services, manufacturing, entertainment, and tech industries.
EDR Platforms in the Crosshairs:
Trend Micro researchers observed recent attacks when Crypto24 actors remotely uninstalled Trend Vision One from a network share using the custom version of RealBlindingEDR and a legitimate group policy utility called gpscript.exe.
The report noted that the attackers use a Trend Vision One uninstaller, XBCUninstaller.exe, which is a legitimate tool provided by the cybersecurity vendor to help customers address issues such as fixing inconsistent agents across deployments.
Trend Micro researchers said the attackers were only able to use the uninstaller, which requires administrator privileges, after gaining elevated privileges through previous malicious activity on compromised systems.
“What we observed represents a classic example of ‘living off the land’ tactics, where threat actors leverage legitimate administrative tools to further their attacks in post-compromise scenarios,” the researchers wrote. “In this case, they used our own maintenance tool to disable endpoint protection before moving laterally to other devices.”
The report emphasized that “properly configured” systems with strong access controls and principle of least privilege will prevent the Crypto24 attacks. But the latest example of the ongoing assault against EDR technology is concerning because it’s clear that threat actors have studied and analyzed these products and found weaknesses to exploit.
“The attackers demonstrate a clear understanding of enterprise defense stacks and an ability to circumvent them,” the researchers wrote.
Additionally, it’s unclear what vulnerable drivers that Crypto24 operators have weaponized for their customized version of RealBlindingEDR, so organizations can’t determine which malicious drivers should be added to blocklists.
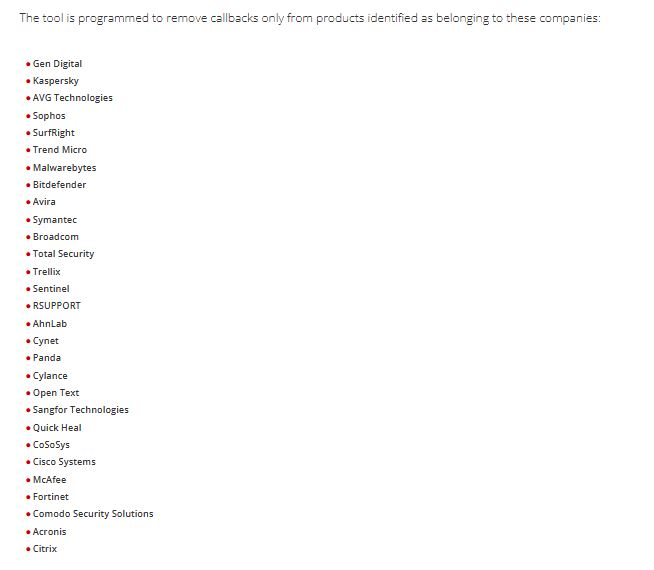
And Trend Micro isn’t the only vendor affected by these attacks. The report noted that the RealBlindingEDR version removes callbacks for security products from nearly 30 vendors, including Cisco, Kaspersky Lab, MalwareBytes, Sophos, and Trellix.
Defending Against Crypto24:
Trend Micro warned that Crypto24 is going big game hunting and urged enterprises to shore up defenses.
“Crypto24 has been targeting high-profile entities within large corporations and enterprise-level organizations,” the report said. “The scale and sophistication of recent attacks indicate a deliberate focus on organizations possessing substantial operational and financial assets.”
In addition to implementing strong access controls and applying the principle of least privilege across the network, Trend Micro urged customers to apply anti-tampering countermeasures to prevent Crypto24 actors from disabling and removing security products.
“Enabling agent self-protection on Windows prevents local users from tampering or removing Trend’s agent,” the researchers said. “Furthermore, activating Trend’s Self-Protection feature ensures that local users cannot tamper with or uninstall any Trend products, preserving endpoint integrity and safeguarding critical security controls.”
Trend Micro also recommended organizations take additional steps such as regularly auditing privileged accounts; limiting remote desktop protocol and remote tool usage to authorized systems only; and regularly inspect scheduled tasks and service creations for signs of malicious activity.
Trend Vision One Threat Insights
Emerging Threats: Decrypting the Encryptors: Crypto24’s Campaign TTPs, Timeline, and Attack Chain
Trend Vision One Intelligence Reports (IOC Sweeping)
Decrypting the Encryptors: Crypto24’s Campaign TTPs, Timeline, and Attack Chain
HexStrike AI Connects ChatGPT, Claude, Copilot with 150+ Security Tools
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind