Hackers are exploiting a recently revealed RCE vulnerability in Zimbra email servers that can be activated by sending specially crafted emails to the SMTP server.
CVE-2024-45519 is a remote code execution vulnerability in Zimbra’s postjournal service, which handles incoming emails via SMTP. Attackers can exploit this flaw by sending emails with commands in the CC field, causing the postjournal service to execute those commands.
Threat actors began exploiting the vulnerability after Project Discovery released its technical details and proof of concept (PoC) exploit code.
“Zimbra, a widely used email and collaboration platform, recently released a critical security update addressing a severe vulnerability in its postjournal service. This vulnerability, identified as CVE-2024-45519, allows unauthenticated attackers to execute arbitrary commands on affected Zimbra installations.” reads a blog post published by Project Discovery.
The vulnerability was discovered by the security researcher lebr0nli (Alan Li). Versions 8.8.15 Patch 46, 9.0.0 Patch 41, 10.0.9, and 10.1.1 released on September 4, 2024 address the vulnerability.
Attackers spoofed Gmail to send emails with base64 strings executed by Zimbra servers. These servers also send exploit emails and host further payloads. The identity of the threat actor behind this campaign remains unclear.
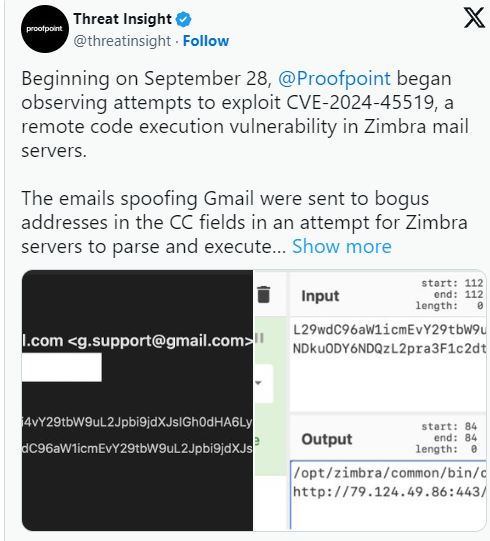
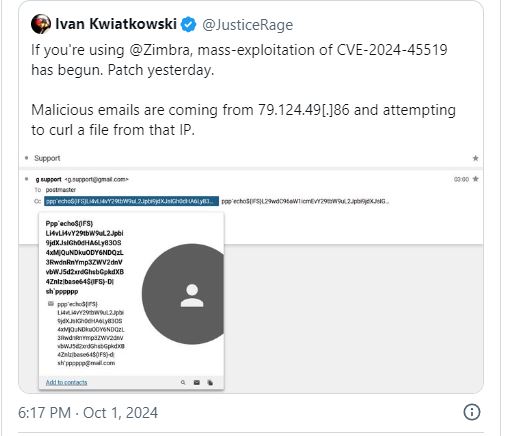
“Beginning on September 28, @Proofpoint began observing attempts to exploit CVE-2024-45519, a remote code execution vulnerability in Zimbra mail servers. The emails spoofing Gmail were sent to bogus addresses in the CC fields in an attempt for Zimbra servers to parse and execute them as commands. The addresses contained base64 strings that are executed with the sh utility.” warned Proofpoint on X. “For unknown reasons, the threat actor is using the same server to send the exploit emails and host second-stage payloads. The activity is unattributed at this time.”
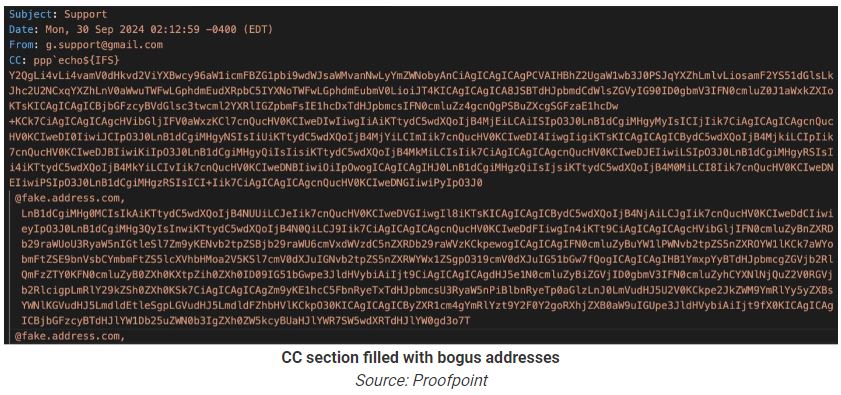
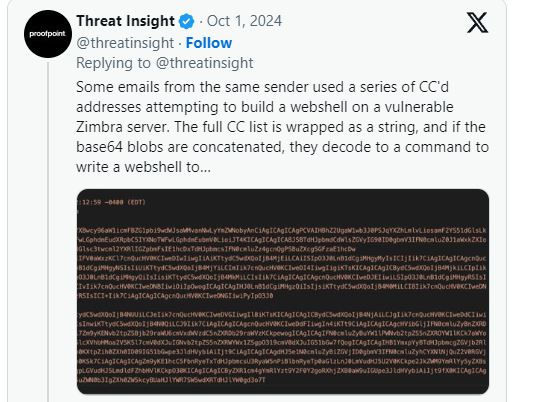
Emails from one sender used CC’d addresses to try to create a webshell on vulnerable Zimbra servers. The attackers combined the CC list into a string, and when decoded from base64, it contained a command to write a webshell at the URL: /jetty/webapps/zimbraAdmin/public/jsp/zimbraConfig.jsp.
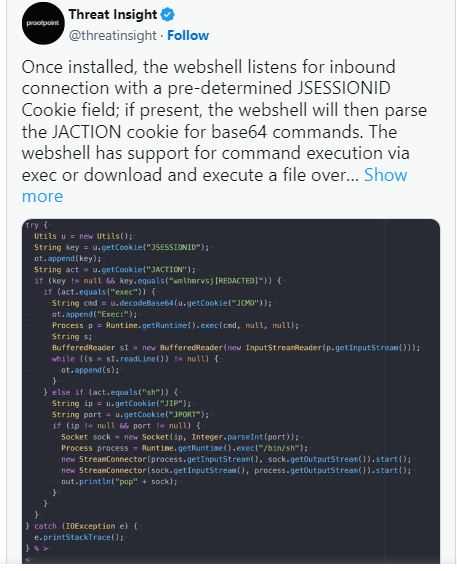
After deployment, the webshell listens for connections using a specific JSESSIONID cookie and interprets the JACTION cookie for base64 commands. It can execute commands or download and run files through a socket connection.
The availability of a PoC exploit exposes users to the risk of attacks, it is strongly recommended to apply the latest versions as soon as possible.
Source: Proofpoint, Securityaffair
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














