Commvault confirmed that a sophisticated cyberattack exploiting a zero-day vulnerability breached its Azure cloud environment earlier this week.
On February 20, 2025, Microsoft notified Commvault of unauthorized activity in its Azure cloud environment.
Commvault announced its immediate response, activating incident protocols and involving leading cybersecurity experts and law enforcement.
By infosecbulletin
/ Friday , June 13 2025
Serious security vulnerabilities in Trend Micro Apex One could allow attackers to inject malicious code and elevate their privileges within...
Read More
By infosecbulletin
/ Thursday , June 12 2025
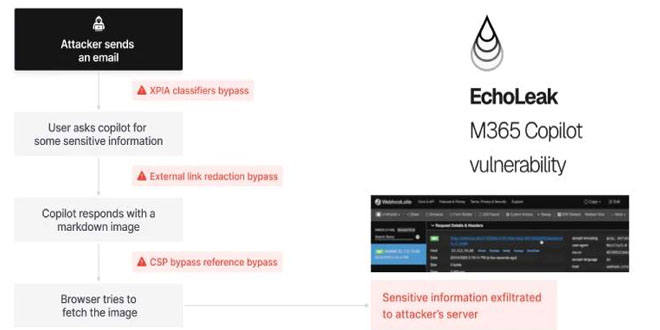
Aim Labs discovered a zero-click AI vulnerability named “EchoLeak” in Microsoft 365 Copilot and reported several ways to exploit it...
Read More
By infosecbulletin
/ Wednesday , June 11 2025
On Tuesday, Adobe released security updates for 254 vulnerabilities in its software, mainly affecting Experience Manager (AEM). There are 254...
Read More
By infosecbulletin
/ Wednesday , June 11 2025
A new report from Bitsight reveals that over 40,000 internet-connected security cameras around the world are exposed, broadcasting live footage...
Read More
By infosecbulletin
/ Wednesday , June 11 2025
Microsoft's June Patch Tuesday update has arrived, addressing 66 vulnerabilities across its product line. One of these flaws was actively...
Read More
By infosecbulletin
/ Tuesday , June 10 2025
More than 84,000 Roundcube webmail installations are at risk due to CVE-2025-49113, a severe remote code execution (RCE) vulnerability that...
Read More
By infosecbulletin
/ Monday , June 9 2025
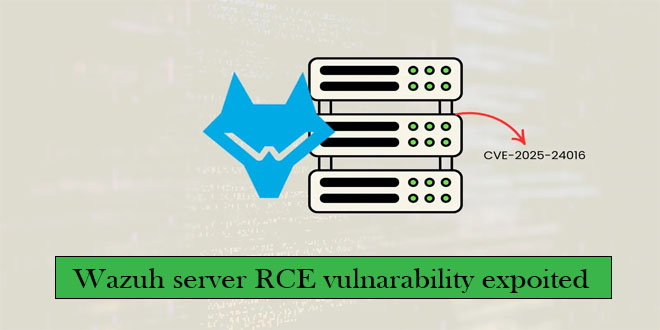
The Security Intelligence and Response Team (SIRT) at Akamai has found that multiple Mirai-based botnets are exploiting CVE-2025-24016, a critical...
Read More
By infosecbulletin
/ Sunday , June 8 2025
On June 5, 2025, CISA released seven advisories regarding Industrial Control Systems (ICS) that highlight current security issues, vulnerabilities, and...
Read More
By infosecbulletin
/ Sunday , June 8 2025
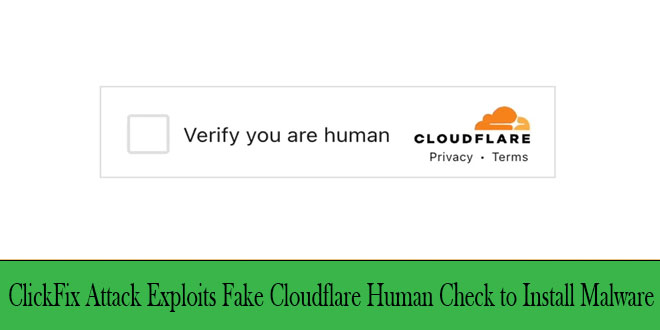
A new social engineering attack uses familiar security checks to trick users into downloading malware via fake Cloudflare verification pages....
Read More
By infosecbulletin
/ Friday , June 6 2025
The Qilin ransomware operation has recently joined attacks exploiting two Fortinet vulnerabilities that allow bypassing authentication on vulnerable devices and...
Read More
The statment reads, “On February 20, 2025, Microsoft notified us about unauthorized activity within our Azure environment by a suspected nation-state threat actor. We immediately activated our incident response plan with the assistance of leading cybersecurity experts and law enforcement.
Our investigation validated that unauthorized access affected a handful of customers and we promptly contacted them to provide assistance. Our investigation also confirmed there was no unauthorized access to any data that Commvault protects for any customer, and no impact on Commvault’s business operations or ability to deliver our products and services.
Action Taken
Our forensic investigation discovered that the threat actor exploited a zero-day vulnerability, which has been patched and we encourage our software customers to do the same. We also rotated affected credentials, continue to further harden our defenses and work with law enforcement.
Working Together
No company is immune to an attack. We believe that sharing information and working together makes us all more resilient. We thank Microsoft for their notification to us, our cybersecurity experts for their trusted partnership, and our customers for their responsiveness and resilience.”
This incident highlights the ongoing and changing nature of cyber threats facing cloud services and managed providers.
Commvault seeks to enhance transparency and encourage collaboration in cybersecurity by sharing details about the breach and its response.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind