Cisco Talos researchers have discovered an ongoing espionage campaign since 2022, targeting telecom and manufacturing sectors in Central and South Asia. The campaign uses a new variant of the PlugX backdoor, closely related to the RainyDay and Turian malware families linked to Chinese-speaking APT groups.
According to the report, “Cisco Talos discovered a new campaign active since 2022, targeting the telecommunications and manufacturing sectors in Central and South Asian countries, delivering a new variant of PlugX.”
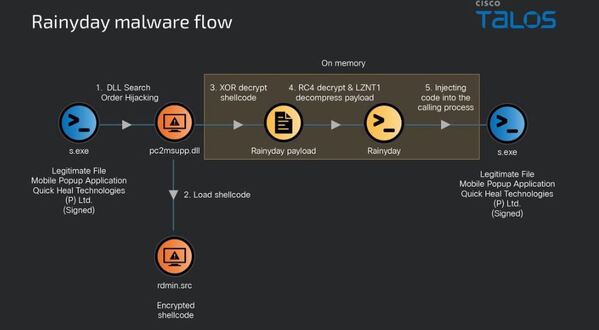
The newly discovered PlugX variant isn’t just another fork of the notorious RAT — it borrows heavily from other espionage toolkits. Talos notes that, “the new variant’s features overlap with both the RainyDay and Turian backdoors, including abuse of the same legitimate applications for DLL sideloading, the XOR-RC4-RtlDecompressBuffer algorithm used to encrypt/decrypt payloads and the RC4 keys used.”
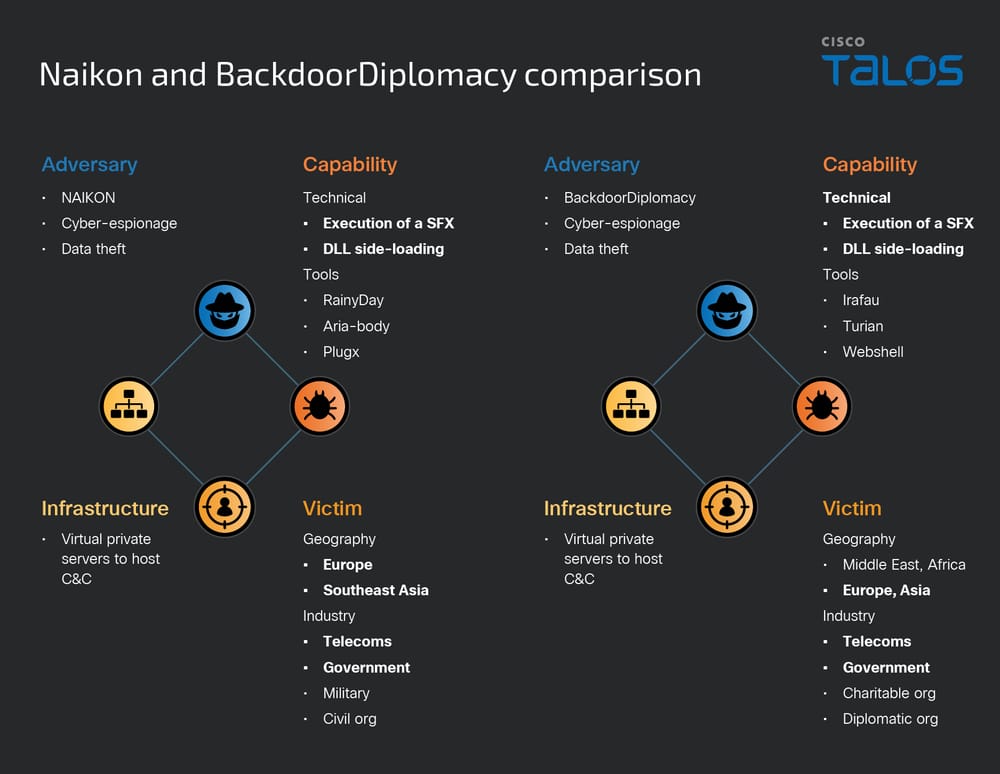
These similarities imply either a common source providing services to different groups or that Naikon and BackdoorDiplomacy might be one and the same.
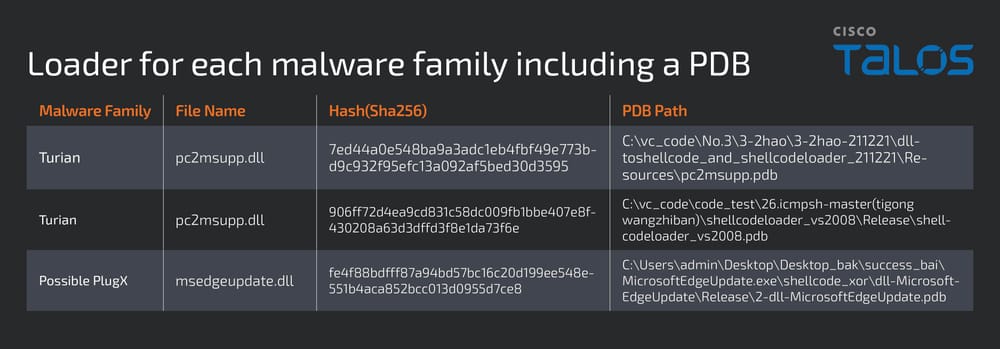
The campaign’s unique PlugX configuration format provided key attribution clues. Unlike standard PlugX builds, this variant mirrors the RainyDay configuration structure, leading Talos to assess “with medium confidence that this variant of PlugX can be attributed to Naikon.”
Naikon, a Chinese espionage group active since 2010, has often targeted government, military, and telecom sectors in Asia. The PlugX variant is part of Naikon’s tools.
The most interesting finding is the overlap between Naikon and BackdoorDiplomacy, another APT group that uses the Turian backdoor.
Talos researchers explain: “Our analysis of the victimology and technical malware implementation has uncovered evidence that indicates a potential connection between the two threat actors and suggests that they are the same group or that both are sourcing their tools from the same vendor.”
Both groups continue to prioritize telecom targets in South and Central Asia, with campaigns sometimes hitting adjacent countries — a pattern consistent with long-term, regionally focused espionage.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind