Renowned cybersecurity researcher Jeremiah Fowler uncovered a non-password-protected database having over 1.1 million records linked to Conduitor Limited (Forces Penpals). This platform provides dating services and social networking for US and UK military personnel and their supporters. Jeremiah Fowler revealed that the publicly accessible database lacked password protection and encryption. …
Read More »
WSJ reports
T-Mobile hacked in massive breach of telecom networks
The Wall Street Journal reported on Friday citing people familiar with the matter that T-Mobile’s network was among the systems hacked in a damaging Chinese cyber-espionage operation that successfully gained entry into multiple U.S. and international telecommunications companies. Hackers were able to breach T-Mobile as part of a monthslong campaign …
Read More »Palo Alto Networks Confirms critical RCE zero-day actively exploited
“Palo Alto Networks has observed threat activity exploiting an unauthenticated remote command execution vulnerability against a limited number of firewall management interfaces which are exposed to the Internet. We are actively investigating this activity,” reads the security bulletin by the cybersecurity provider Palo Alto Networks. On November 8, Palo Alto …
Read More »
CISA, FBI Warns
Hacker compromised multiple teleco network at US
US authorities have revealed a major cyberespionage campaign by hackers, targeting information from Americans in government and politics. The FBI and the Cybersecurity and Infrastructure Security Agency (CISA) said in a joint statement on Wednesday that actors affiliated with Beijing had “compromised networks at multiple telecommunications companies”. In a statement …
Read More »Bitdefender releases free decryptor for ShrinkLocker ransomware
Bitdefender has released a decryptor for the ShrinkLocker ransomware after months of concern from responders regarding attacks involving this malware. Bitdefender released a detailed blog explaining how a ransomware strain utilizes Microsoft’s BitLocker to encrypt files and removes recovery options. “ShrinkLocker is a novel ransomware strain that leverages a unique …
Read More »Russia blocks thousands websites using Cloudflare’s privacy service
Russia’s media censor, Roskomnadzor, has blocked thousands of local websites using Cloudflare’s encryption feature that enhances online privacy and security. Local media reports indicate that several websites were blocked overnight on October 6. These sites use Cloudflare’s Encrypted Client Hello (ECH) feature, which enhances user privacy by making it harder …
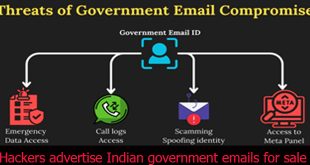
Read More »Hacker to sale Indian Gov.t email credentials
Advertisement for selling the credentials of allegedly belonging to Indian government emails surfaced on the dark web marketplace. A hacker on a private forum claims that purchasing access to these government email accounts can make anyone willing to pay a few thousand rupees “become” a government officer. The forum post …
Read More »Hacker claim data breach: bank confirms blaming third party
Interbank, a major financial institution in Peru, has confirmed a data breach after a hacker leaked stolen data online. Formerly the International Bank of Peru, the company offers financial services to over 2 million customers. “To our clients: We regret this situation and understand the inconvenience this may cause you. …
Read More »CISA Launches Its First Ever International Strategic Plan
The US Cybersecurity and Infrastructure Security Agency (CISA) has released its first international strategic plan to enhance global cooperation in addressing cyber threats to critical infrastructure. The plan recognizes that cyber risks are complex and spread across different regions, highlighting the importance of quickly sharing threat information and risk reduction …
Read More »Unprotected UN Database Exposes 228GB of Gender Violence Victims’ Data
Cybersecurity researcher Jeremiah Fowler found a non-password-protected database with 115,000 records linked to the UN Trust Fund to End Violence against Women. This fund aims to prevent violence against women and girls by supporting organizations that address gender-based violence and promote women’s rights. The unprotected database contained sensitive financial reports, …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind