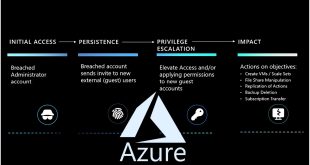
Microsoft security experts recently conducted an exploration on how to effectively use Azure Logs to identify and counteract threat actions. Azure’s defense mechanism relies on effectively understanding and using logs to hunt for threats. Microsoft focuses on integrating best practices for log management, analysis, and incident response to stay proactive …
Read More »
NCSC
NEW UK LAW BANS DEFAULT PASSWORDS ON SMART DEVICES
The UK’s NCSC wants smart device manufacturers to follow new law banning default passwords. The law, known as the Product Security and Telecommunications Infrastructure act (or PSTI act), will be effective on April 29, 2024. “From 29 April 2024, manufacturers of consumer ‘smart’ devices must comply with new UK law.” …
Read More »U.S. Releases New AI Security Guidelines for Critical Infrastructure
DHS with Cybersecurity and Infrastructure Security Agency (CISA) have released safety and security guidelines to address AI risks that affect the safety and security of critical infrastructure systems in the US. The guidelines analyze system-level risks in three main categories. Attacks Using AI: The use of AI to enhance, plan, …
Read More »Chinese Botnet As-A-Service Bypasses Cloudflare & Other DDoS Protection Services
Earlier this week, EPCYBER has identified a large scale network of Chinese botnet as-a-service which consists of various domains, over 20 active telegram groups and other domestic communication channels using Chinese infrastructure. It is evident that the methods and botnet developed and used by the group, successfully bypasses latest DDoS …
Read More »
ALERT: SEKOIA REPORT
PlugX Malware Plagues Over 90k IP Addresses over 170 countries
The worm was first discovered in a 2023 post by security firm Sophos. It became active in 2019 when a variant of malware called PlugX added a feature to infect USB drives automatically. This allowed the malware to spread to new machines without needing any user interaction. Sekoia, a European …
Read More »Palo Alto network shared latest remediation of CVE-2024-3400
Palo Alto Networks has given urgent advice to the remediation of a critical vulnerability, known as CVE-2024-3400, which attackers have used to get unauthorized access. The cybersecurity company has provided clear steps for organizations to reduce the risks of this breach and protect their networks from future attacks. Environment: Palo …
Read More »CISA Launches Ransomware Vulnerability Warning Pilot for Critical Infrastructure
Organizations across all sectors and of all sizes are too frequently impacted by damaging ransomware incidents. Many of these incidents are perpetrated by ransomware threat actors using known vulnerabilities. By urgently fixing these vulnerabilities, organizations can significantly reduce their likelihood of experiencing a ransomware event. In addition, organizations should implement …
Read More »WhatsApp warns India to exit, If…
According to the report by several Indian media, social media platform Meta will withdraw its entire service from India if it is forced to breaks encryption. This is what WhatsApp has claimed in the hearing of a case in the Delhi High Court. This was claimed by WhatsApp in the …
Read More »Bad actor threat to expose BSNL 2.9 million data
Platform BreachForum, bad actor perell, same person who claimed to expose the data of “Bharat Sanchar Nigam Limited” BSNL for the second time. The threat actor claimed first December-3, 2023 where he wrote “India’s 4th most popular telecommunications company has suffered a substantial data breach” and he claimed to have …
Read More »India’s ICICI Bank exposed thousands of credit cards to ‘wrong’ users
“Our customers are our utmost priority and we are wholeheartedly dedicated to safe guarding their interests. It has come to our notice that about 17,000 new credit cards which were issued in the past few days were erroneously mapped in our digital channels to wrong users. They constitute about 0.1% …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind