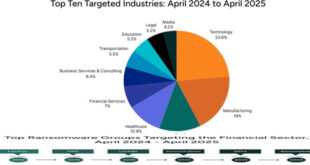
From April 2024 to April 2025, Flashpoint analysts noted that the financial sector was a major target for threat actors, with 406 incidents publicly reported as ransomware attacks, accounting for seven percent of all ransomware incidents during that time. Why Finance? The financial sector consistently ranks as one of the …
Read More »Commvault Confirms Its Azure Cloud Environment Breach via Zero-Day Attack
Commvault confirmed that a sophisticated cyberattack exploiting a zero-day vulnerability breached its Azure cloud environment earlier this week. On February 20, 2025, Microsoft notified Commvault of unauthorized activity in its Azure cloud environment. Commvault announced its immediate response, activating incident protocols and involving leading cybersecurity experts and law enforcement. The …
Read More »Ransomware Attack On Biopharma : Hacker seeks $80k
Indian Pimpri Chinchwad police’s cyber cell is looking into a complaint where a hacker demanded $80,000 (over Rs 68 lakh) from a biopharmaceutical company in Hinjewadi to release encrypted data he had stolen. A senior employee contacted the police on Monday following a threatening email received on April 27. A …
Read More »Ticket resaler exposed 520,054 records size of 200 GB
Cybersecurity researcher Jeremiah Fowler discovered a non-password-protected database with 520,054 records from an event ticket resale platform and reported it to vpnMentor. The unprotected public database had 520,054 records totaling 200 GB. It was labeled as containing customer inventory files in PDF, JPG, PNG, and JSON formats. A review of …
Read More »Massive Attack: Hacker Actively Use 4800+ IPs To Attack Git Configuration Files
A recent increase in cyber reconnaissance has endangered thousands of organizations, as GreyNoise, a global threat intelligence platform, reported a significant rise in attempts to access sensitive Git configuration files. On April 20 and 21, GreyNoise recorded over 4,800 unique IPs targeting these files, marking a record high and indicating …
Read More »‘SessionShark’ ToolKit Bypasses Microsoft Office 365 MFA
The SessionShark phishing kit bypasses Office 365 MFA by stealing session tokens. Experts warn about real-time attacks using fake login pages and Telegram alerts. SlashNext security experts have found a new tool, “SessionShark,” used by cyber criminals to steal Microsoft Office 365 login information. It can bypass multi-factor authentication (MFA), …
Read More »ISPAB president “whatsapp” got hacked via phishing link
Imdadul Haque, the president of Internet Service Provider of Bangladesh (ISPAB) said, I automatically got back my WhatsApp account. What happened: A media worker from Bangladesh shared a screen shot with infosecbulletin. “Can I urgently send 2000 taka to bKash now? I will give it tomorrow morning, InshaAllah.” The reporter …
Read More »Hackers Exploit Zoom’s Remote Control Feature for System Access
ELUSIVE COMET is a threat actor conducting a sophisticated attack campaign that uses Zoom’s remote control feature to access victims’ computers without permission. The ELUSIVE COMET operation begins with attackers masquerading as legitimate media organizations, specifically “Bloomberg Crypto,” to invite high-profile targets for interviews. Invitations are sent through social media, …
Read More »UK Software Firm Exposed 8 million of Healthcare Worker Records
A data leak involving 8 million UK healthcare worker records, including IDs and financial information, was caused by a misconfigured database from the UK software firm Logezy, which specializes in employee data management. Cybersecurity researcher Jeremiah Fowler from vpnMentor discovered this issue. Fowler’s investigation found nearly 8 million unprotected records, …
Read More »Bengaluru firm got ransomware attack, Hacker demanded $70,000
Bengaluru’s Whiteboard Technologies Pvt Ltd was hit by a ransomware attack, with hackers demanding a ransom of up to $70,000 (around ₹60.26 lakh) to unlock encrypted files and prevent data leaks. The breach happened on March 31, between 4:23 PM and 5 PM, and was reported to authorities on April …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind