A threat actor claims to have breached Link3, a major IT solutions and internet service provider based in Bangladesh. The data has been put up for sale on a dark web forum. According to the forum post: Link3 is the largest ISP in the country by active subscribers, offering essential …
Read More »AI Pentesting Tool ‘Villager’ Merges Kali Linux with DeepSeek AI for Automated Attacks
The Villager framework, an AI-powered penetration testing tool, integrates Kali Linux tools with DeepSeek AI to automate cyber attack processes. Developed by the Chinese group Cyberspike, it was released on the Python Package Index in July 2025 and quickly gained over 10,000 downloads in two months. Villager marks a major …
Read More »CyberVolk Ransomware Attacks CII In Japan, France, and UK
CyberVolk ransomware, which appeared in May 2024, has increased attacks on government agencies and critical infrastructures in Japan, France, and the UK. CyberVolk, with pro-Russian views, targets countries seen as threats to Russia using advanced encryption that is very hard to break. This article analyzes CyberVolk’s encryption system, its execution …
Read More »
(CVE-2025-10159)
Sophos Addressed Critical Auth Bypass flaw in Wireless Access Points
Sophos fixed an authentication bypass vulnerability in its AP6 Series Wireless Access Points, preventing attackers from obtaining admin privileges. The company found the issue during internal security tests and has issued a firmware update to fix it. An attacker with network access to the access point’s management IP can bypass …
Read More »1.6M fitness phone call recordings exposed online
Security researcher Jeremiah Fowler discovered a database containing sensitive information from gym customers and staff, including names, financial details, and possible phone call, left unencrypted and unprotected. Jeremiah Fowler claims he discovered the wide-open AWS repository managed by HelloGym in late July. The database was open for a week, and …
Read More »Elastic Security Incident : Hackers Accessed Email Account Contains Valid Credentials
Elastic reported a security incident caused by a breach at Salesloft Drift, leading to unauthorized access to an internal email account with valid credentials. The company’s main Salesforce system was unaffected, but the incident revealed sensitive information in a few emails. Salesloft Drift reported a security incident affecting its platform …
Read More »Hacker Exploit Amazon SES to Send 50K Phishing Emails
Researchers at Wiz discovered a complex phishing campaign using Amazon’s Simple Email Service (SES) for large-scale attacks, showing how hacked cloud credentials can evade standard email security measures. The attack, identified in May 2025, began with stolen AWS access keys a common attack vector that Wiz observes “tens of newly …
Read More »
SafePay Ransomware
SafePay Ransomware Attacks 73 Orgs in a Single Month
The global ransomware landscape continues to shift in 2025, with SafePay rapidly emerging as one of the most active and disruptive groups. In June, SafePay claimed responsibility for attacks on 73 victim organizations, a record-breaking monthly tally that placed it at the top of Bitdefender’s Threat Debrief rankings. The surge …
Read More »
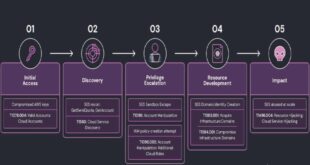
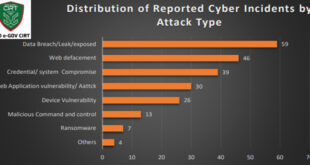
Bangladesh Cyber Threat Landscape- 2024
602 Vuln exploited: Afftected daily 905 IP In Bangladesh in 2024
Bangladesh Cyber Threat Landscape 2024, by BGD e-GOV CIRT, reveals a sharp escalation in cyber threats across Bangladesh. The year saw a surge in ransomware, phishing, hacktivism, and data breaches, affecting both public and private sectors. Critical vulnerabilities in outdated systems, increased use of the dark web for trading stolen …
Read More »AI-powered malware hit 2,180 GitHub accounts in “s1ngularity” attack
Investigations into the Nx “s1ngularity” NPM supply chain attack have unveiled a massive fallout, with thousands of account tokens and repository secrets leaked. According to a post-incident evaluation by Wiz researchers, the Nx compromise has resulted in the exposure of 2,180 accounts and 7,200 repositories across three distinct phases. Wiz …
Read More » InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind