The FBI has alerted that cyber actors have compromised over 260,000 internet-connected devices, mainly routers, to form a large botnet for malicious activities, including distributed denial of service attacks and identity concealment.
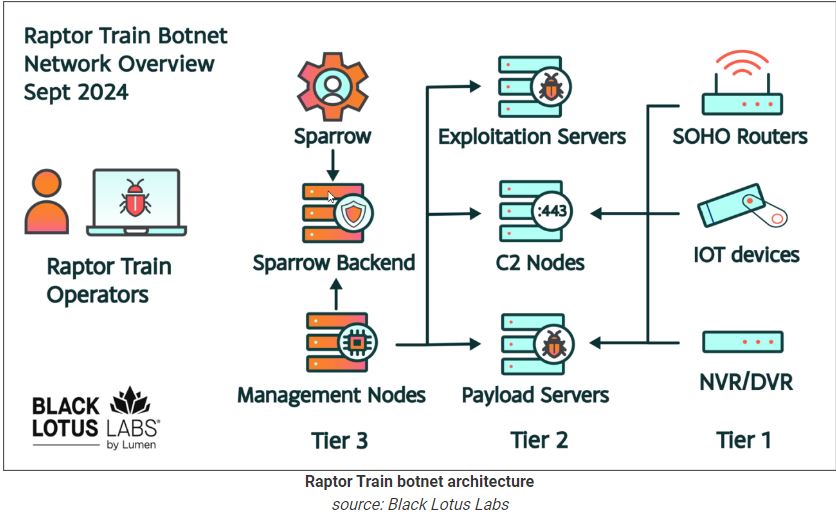
The FBI advisory states that a botnet, managed by the China-based Integrity Technology Group, has been active since mid-2021.
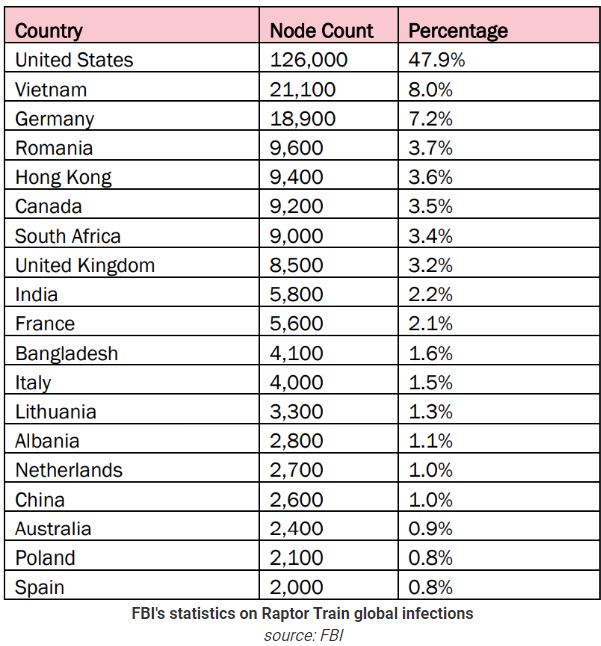
The botnet is primarily active in the US, with 126,000 compromised devices as of June 2024, followed by Vietnam with 21,100 and Germany with 18,900.
The main targets of the threat actor are small office/home office (SOHO) routers, firewalls, network-attached storage (NAS), and Internet of Things (IoT) devices like webcams and IP cameras. While many of these devices are outdated, a significant portion of the botnet includes those still supported by their vendors.
“This botnet infrastructure is comprised of a network of devices, known as “bots,” which are infected with a type of malware that provides threat actors with unauthorized remote access,” the advisory reads.
The FBI reports that IP addresses from China Unicom’s Beijing network, linked to a botnet, were also involved in hacking activities against US targets. This is connected to the threat group known as Flax Typhoon, RedJuliett, and Ethereal Panda.
According to Reuters, the FBI has neutralized a threat actor by seizing thousands of compromised devices. This operation is similar to the one against Volt Typhoon earlier this year.
The threat actor uses Mirai malware to take control of devices. Its source code was made public in 2016, leading to the use of Mirai botnets for various malicious activities.
“To recruit a new “bot,” the botnet system first compromises an internet-connected device using one of a variety of known vulnerability exploits. Post-compromise, the victim device executes a Mirai-based malware payload from a remote server,” the FBI explains.
More than 80 subdomains of “w8510.com” connected to the botnet’s command and control servers, along with other domains. Researchers found databases on these servers containing over 1.2 million records of compromised devices, including 385,000 unique devices belonging to victims in the US.
The threat actor is expanding the botnet, now using at least 50 different versions of Linux.
The FBI advises device owners and network defenders to take steps to prevent IoT devices from joining a botnet.
Recommended mitigations include disabling unused services and ports, implementing network segmentation, monitoring high network traffic, promptly applying patches and updates, using strong passwords instead of defaults, periodically rebooting devices, and replacing outdated equipment.
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind














