A sophisticated cyber fraud has stolen over ₹5.58 crore from many bank accounts, highlighting serious concerns about digital payment security. This scam involved cloning biometric data and affected 251 accounts in 17 districts. Authorities are working hard to contain the situation and catch those responsible.
The Modus Operandi: A Digital Heist
By infosecbulletin
/ Tuesday , August 12 2025
In early August 2025, cybersecurity teams in Türkiye detected a new Java-based loader that avoided detection by all public sandboxes,...
Read More
By infosecbulletin
/ Monday , August 11 2025
ESET researchers found a zero-day vulnerability in WinRAR for Windows, tracked as CVE-2025-8088, which has been used to run malicious...
Read More
By infosecbulletin
/ Sunday , August 10 2025
A sophisticated cyber fraud has stolen over ₹5.58 crore from many bank accounts, highlighting serious concerns about digital payment security....
Read More
By infosecbulletin
/ Sunday , August 10 2025
Google confirmed that a recent data breach in one of its Salesforce CRM systems exposed information about potential Google Ads...
Read More
By infosecbulletin
/ Saturday , August 9 2025
More than 28,000 unpatched Microsoft Exchange servers are publicly accessible and vulnerable to the critical security flaw CVE-2025-53786, as reported...
Read More
By infosecbulletin
/ Saturday , August 9 2025
Google has unveiled its best practices aimed at thwarting dangling bucket takeovers, encouraging developers to fortify their cloud environments. The...
Read More
By infosecbulletin
/ Saturday , August 9 2025
Researchers revealed critical zero-day vulnerabilities that bypass Windows BitLocker encryption, enabling attackers with physical access to quickly extract data from...
Read More
By infosecbulletin
/ Friday , August 8 2025
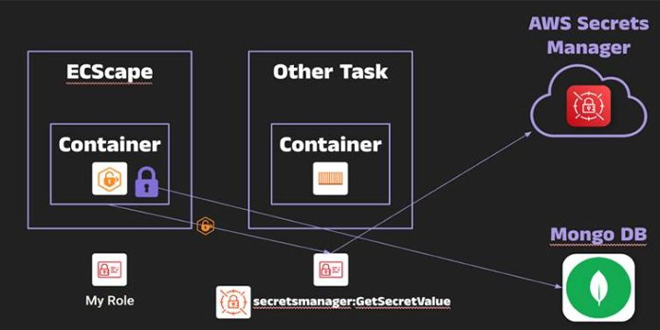
Security researchers disclosed a cirtical flaw in Amazon Elastic Container Service (ECS) that enables harmful containers to steal AWS credentials...
Read More
By infosecbulletin
/ Friday , August 8 2025
Let’s look at 7 tools for automating patch deployment. Each tool offers unique features for various environments, from small DevOps...
Read More
By infosecbulletin
/ Friday , August 8 2025
Germany's top court ruled on Thursday that police can secretly install spy software on phones and computers only for serious...
Read More
Fraudsters exploited a crucial vulnerability in the Aadhaar payment system to clone biometric data and unlawfully access victims’ bank accounts. Most victims were rural residents dependent on local businesses for banking, whose fingerprints and personal information were stolen without their consent. The fraudulent transactions were carried out using business units linked to Fino Payments Bank Limited, which serves remote areas.
A Widespread Network of Deception
The fraud covers 17 districts in Bihar, India, with Araria as the main hub, losing over ₹3.05 crore from 140 accounts. Purnia and Kishanganj also faced significant losses of ₹99.87 lakh and ₹69.82 lakh, respectively. This widespread crime indicates a well-organized and skilled criminal network.
The Human Cost: A Community in Crisis
Most fraud victims come from marginalized communities, losing a significant portion of their savings. Many discovered their accounts empty after depositing their earnings, causing great distress. Complaints have been filed with the National Cyber Crime Reporting Portal (NCRCP), but only a small fraction of the money has been recovered, leaving many in despair.
Questions of Security and Accountability
The bank has reported a leak of confidential customer data, leading to an investigation by the Economic Offences Unit (EOU) of the Bihar Police. The bank is worried about the local police’s slow response and is keen to identify those responsible to prevent further misuse.
Google alerts of cloud storage bucket hijacking attacks
 InfoSecBulletin Cybersecurity for mankind
InfoSecBulletin Cybersecurity for mankind